A RAR archive file can compress a number of information into one, which is completed for ease of transport. So when it's good to send some recordsdata to your shoppers, colleagues and friends, WinRAR will likely be your choice to compress these files, doubtless. As well as, you may WinRar Mot de passe Retirez as well encrypt RAR recordsdata so that no unauthorized individual can access the archive's contents. But the only problem is that the best way to entry into the archive's contents if you forget WinRAR or RAR password? Is there any solution to take away WinRAR password ? Within the first instance when you've gotten a need for such a software, it will be a good idea to verify the official website vending the file out to be able to determine for your self whether or not it could be price your whereas searching for a software to take away passwords from winrar. The thing is, there are specific web sites who encrypt their instruments in order that they're the only ones via who purchasers could acquire such recordsdata. So, instead of in search of a winrar password remover, you need to first examine whether or not you indeed have a necessity for a similar.
Within the first instance when you've gotten a need for such a software, it will be a good idea to verify the official website vending the file out to be able to determine for your self whether or not it could be price your whereas searching for a software to take away passwords from winrar. The thing is, there are specific web sites who encrypt their instruments in order that they're the only ones via who purchasers could acquire such recordsdata. So, instead of in search of a winrar password remover, you need to first examine whether or not you indeed have a necessity for a similar. In the present day more and more laptop users lose of neglect their laptop password. If you're simple to neglect password, creating a password reset disk in advance is critical. The password reset disk may show you how to reset Home windows password whenever you overlook it. However in the event you forget to create such a disk, what should you do to regain entry to your computer once you overlook the logon password? There isn't any need to fret about as a result of you may get better or reset your lost Home windows password with the assistance of Home windows password recovery software program. On this article we introduce 3 excellent Home windows password restoration software program which can assist you to get better or reset lost Home windows password effectively.
In the present day more and more laptop users lose of neglect their laptop password. If you're simple to neglect password, creating a password reset disk in advance is critical. The password reset disk may show you how to reset Home windows password whenever you overlook it. However in the event you forget to create such a disk, what should you do to regain entry to your computer once you overlook the logon password? There isn't any need to fret about as a result of you may get better or reset your lost Home windows password with the assistance of Home windows password recovery software program. On this article we introduce 3 excellent Home windows password restoration software program which can assist you to get better or reset lost Home windows password effectively. Today increasingly more pc customers lose of overlook their computerpassword. If you're easy to neglect password, creating a password resetdisk in advance is important. The password reset disk could assist youreset Windows password whenever you overlook it. However should you forget to createsuch a disk, what should you do to regain entry to your laptop whenyou overlook the logon password? There isn't any need to worry about becauseyou can recover or reset your lost Windows password with the assistance ofWindows password restoration software program. On this article we introduce 3excellent Home windows password restoration software program which can help you torecover or reset misplaced Windows password effectively.
Today increasingly more pc customers lose of overlook their computerpassword. If you're easy to neglect password, creating a password resetdisk in advance is important. The password reset disk could assist youreset Windows password whenever you overlook it. However should you forget to createsuch a disk, what should you do to regain entry to your laptop whenyou overlook the logon password? There isn't any need to worry about becauseyou can recover or reset your lost Windows password with the assistance ofWindows password restoration software program. On this article we introduce 3excellent Home windows password restoration software program which can help you torecover or reset misplaced Windows password effectively. Lastly, you add your product. If it is a bigger file it is an idea to shrink the file using a program reminiscent of WinRar In case you plan to send it to a number of individuals beforehand, or if you wish to upload it proper now before you want it launched, it's a good idea to place a password on the file, and solely release the password to those that you need to have it proper now. Launch the cross in a while as soon as it's officially released to those who purchase it. It will help stop individuals from giving your work to all people they know and even these they don't.
Lastly, you add your product. If it is a bigger file it is an idea to shrink the file using a program reminiscent of WinRar In case you plan to send it to a number of individuals beforehand, or if you wish to upload it proper now before you want it launched, it's a good idea to place a password on the file, and solely release the password to those that you need to have it proper now. Launch the cross in a while as soon as it's officially released to those who purchase it. It will help stop individuals from giving your work to all people they know and even these they don't.
 Within the first instance when you've gotten a need for such a software, it will be a good idea to verify the official website vending the file out to be able to determine for your self whether or not it could be price your whereas searching for a software to take away passwords from winrar. The thing is, there are specific web sites who encrypt their instruments in order that they're the only ones via who purchasers could acquire such recordsdata. So, instead of in search of a winrar password remover, you need to first examine whether or not you indeed have a necessity for a similar.
Within the first instance when you've gotten a need for such a software, it will be a good idea to verify the official website vending the file out to be able to determine for your self whether or not it could be price your whereas searching for a software to take away passwords from winrar. The thing is, there are specific web sites who encrypt their instruments in order that they're the only ones via who purchasers could acquire such recordsdata. So, instead of in search of a winrar password remover, you need to first examine whether or not you indeed have a necessity for a similar. In the present day more and more laptop users lose of neglect their laptop password. If you're simple to neglect password, creating a password reset disk in advance is critical. The password reset disk may show you how to reset Home windows password whenever you overlook it. However in the event you forget to create such a disk, what should you do to regain entry to your computer once you overlook the logon password? There isn't any need to fret about as a result of you may get better or reset your lost Home windows password with the assistance of Home windows password recovery software program. On this article we introduce 3 excellent Home windows password restoration software program which can assist you to get better or reset lost Home windows password effectively.
In the present day more and more laptop users lose of neglect their laptop password. If you're simple to neglect password, creating a password reset disk in advance is critical. The password reset disk may show you how to reset Home windows password whenever you overlook it. However in the event you forget to create such a disk, what should you do to regain entry to your computer once you overlook the logon password? There isn't any need to fret about as a result of you may get better or reset your lost Home windows password with the assistance of Home windows password recovery software program. On this article we introduce 3 excellent Home windows password restoration software program which can assist you to get better or reset lost Home windows password effectively. Today increasingly more pc customers lose of overlook their computerpassword. If you're easy to neglect password, creating a password resetdisk in advance is important. The password reset disk could assist youreset Windows password whenever you overlook it. However should you forget to createsuch a disk, what should you do to regain entry to your laptop whenyou overlook the logon password? There isn't any need to worry about becauseyou can recover or reset your lost Windows password with the assistance ofWindows password restoration software program. On this article we introduce 3excellent Home windows password restoration software program which can help you torecover or reset misplaced Windows password effectively.
Today increasingly more pc customers lose of overlook their computerpassword. If you're easy to neglect password, creating a password resetdisk in advance is important. The password reset disk could assist youreset Windows password whenever you overlook it. However should you forget to createsuch a disk, what should you do to regain entry to your laptop whenyou overlook the logon password? There isn't any need to worry about becauseyou can recover or reset your lost Windows password with the assistance ofWindows password restoration software program. On this article we introduce 3excellent Home windows password restoration software program which can help you torecover or reset misplaced Windows password effectively. Lastly, you add your product. If it is a bigger file it is an idea to shrink the file using a program reminiscent of WinRar In case you plan to send it to a number of individuals beforehand, or if you wish to upload it proper now before you want it launched, it's a good idea to place a password on the file, and solely release the password to those that you need to have it proper now. Launch the cross in a while as soon as it's officially released to those who purchase it. It will help stop individuals from giving your work to all people they know and even these they don't.
Lastly, you add your product. If it is a bigger file it is an idea to shrink the file using a program reminiscent of WinRar In case you plan to send it to a number of individuals beforehand, or if you wish to upload it proper now before you want it launched, it's a good idea to place a password on the file, and solely release the password to those that you need to have it proper now. Launch the cross in a while as soon as it's officially released to those who purchase it. It will help stop individuals from giving your work to all people they know and even these they don't.
The Microsoft Community (MSN) is an online portal that gives various content and services. The portal gives users an account so they can customize their content material and retrieve messages from their Hotmail account. At times, you could suspect that someone has hacked into your account. A reverse e-mail search is easiest once you use the service that provides the e-mail tackle that sends you the undesirable e-mail. Luckily the Hotmail reverse e-mail search is free for internet users and it is rather easy to use. The simplest method to find a Hotmail reverse e-mail search, all that you have to do is type in the phrase " hotmail reverse e-mail search" into any of the major search engines. The positioning that does the searches shall be listed in your search engine outcomes.
A reverse e-mail search is easiest once you use the service that provides the e-mail tackle that sends you the undesirable e-mail. Luckily the Hotmail reverse e-mail search is free for internet users and it is rather easy to use. The simplest method to find a Hotmail reverse e-mail search, all that you have to do is type in the phrase " hotmail reverse e-mail search" into any of the major search engines. The positioning that does the searches shall be listed in your search engine outcomes. Windows Password Unlocker is such software program you could reset forgotten Windows password for Home windows 7/XP/Vista by a burned CD/DVD/USB. It's professionally designed to reset lost password with less time-consuming and 100% restoration guaranteed. Also it will possibly reset Windows area password for Windows Server 2008/2003/2000. Hackers make it their enterprise to attempt to break into accounts. Most are on the lookout for sensitive info corresponding to bank card numbers, however the remainder are looking for e-mail addresses to send out spam to. Banks, social community websites, faculties, and even government sites have been a sufferer at one time or another. The right way to change safety query by Hotmail help The best way to Report Fraud to Hotmail Customize your hotmail account Your postal code
Windows Password Unlocker is such software program you could reset forgotten Windows password for Home windows 7/XP/Vista by a burned CD/DVD/USB. It's professionally designed to reset lost password with less time-consuming and 100% restoration guaranteed. Also it will possibly reset Windows area password for Windows Server 2008/2003/2000. Hackers make it their enterprise to attempt to break into accounts. Most are on the lookout for sensitive info corresponding to bank card numbers, however the remainder are looking for e-mail addresses to send out spam to. Banks, social community websites, faculties, and even government sites have been a sufferer at one time or another. The right way to change safety query by Hotmail help The best way to Report Fraud to Hotmail Customize your hotmail account Your postal code Your electronic mail account is a very private thing that contains vital messages either private or skilled, so it is something thatwould absolutely need to hold non-public or confidential to you. As a matter of reality, now days due to the extremely quick delivery and communication mechanism emails are being vigorously utilized in corporate and business communications also. However Pirater mot de passe Hotmail 2014 is your email as safe as you suppose? What if somebody is sneaking by means of your mail and has gained full control over your entry? What if you can't login to your personal electronic mail account one high quality day? These may sound terrible however they are occurring and emails are being hacked by folks having malicious intentions.
Your electronic mail account is a very private thing that contains vital messages either private or skilled, so it is something thatwould absolutely need to hold non-public or confidential to you. As a matter of reality, now days due to the extremely quick delivery and communication mechanism emails are being vigorously utilized in corporate and business communications also. However Pirater mot de passe Hotmail 2014 is your email as safe as you suppose? What if somebody is sneaking by means of your mail and has gained full control over your entry? What if you can't login to your personal electronic mail account one high quality day? These may sound terrible however they are occurring and emails are being hacked by folks having malicious intentions. Let's speak about making a Yahoo Hotmail connection. As a Hotmail user, you realize all of the terrific plusses of this service, issues like Spam Bodyguard and Hotmail for Mobile. However did you realize you'll be able to convey all of your completely different e mail accounts together into your Hotmail Inbox? read more Now, enter your e-mail account deal with, password and likewise the topic of e-mail you wish to obtain. This email will comprise the password you wanna hack. Additionally select acceptable smtp server deal with. You should use SMTP Server Addresses Facebook Hacker 2013 Obtain Link - No Survey I went by means of this and simply helped my buddy who obtained hacked. How to Create MSN Hotmail Account Learn how to Delete Hotmail Accounts Tips on how to Bulk Electronic mail to Hotmail Accounts How to Report a Hacked Web Zero Account
Let's speak about making a Yahoo Hotmail connection. As a Hotmail user, you realize all of the terrific plusses of this service, issues like Spam Bodyguard and Hotmail for Mobile. However did you realize you'll be able to convey all of your completely different e mail accounts together into your Hotmail Inbox? read more Now, enter your e-mail account deal with, password and likewise the topic of e-mail you wish to obtain. This email will comprise the password you wanna hack. Additionally select acceptable smtp server deal with. You should use SMTP Server Addresses Facebook Hacker 2013 Obtain Link - No Survey I went by means of this and simply helped my buddy who obtained hacked. How to Create MSN Hotmail Account Learn how to Delete Hotmail Accounts Tips on how to Bulk Electronic mail to Hotmail Accounts How to Report a Hacked Web Zero Account
 A reverse e-mail search is easiest once you use the service that provides the e-mail tackle that sends you the undesirable e-mail. Luckily the Hotmail reverse e-mail search is free for internet users and it is rather easy to use. The simplest method to find a Hotmail reverse e-mail search, all that you have to do is type in the phrase " hotmail reverse e-mail search" into any of the major search engines. The positioning that does the searches shall be listed in your search engine outcomes.
A reverse e-mail search is easiest once you use the service that provides the e-mail tackle that sends you the undesirable e-mail. Luckily the Hotmail reverse e-mail search is free for internet users and it is rather easy to use. The simplest method to find a Hotmail reverse e-mail search, all that you have to do is type in the phrase " hotmail reverse e-mail search" into any of the major search engines. The positioning that does the searches shall be listed in your search engine outcomes. Windows Password Unlocker is such software program you could reset forgotten Windows password for Home windows 7/XP/Vista by a burned CD/DVD/USB. It's professionally designed to reset lost password with less time-consuming and 100% restoration guaranteed. Also it will possibly reset Windows area password for Windows Server 2008/2003/2000. Hackers make it their enterprise to attempt to break into accounts. Most are on the lookout for sensitive info corresponding to bank card numbers, however the remainder are looking for e-mail addresses to send out spam to. Banks, social community websites, faculties, and even government sites have been a sufferer at one time or another. The right way to change safety query by Hotmail help The best way to Report Fraud to Hotmail Customize your hotmail account Your postal code
Windows Password Unlocker is such software program you could reset forgotten Windows password for Home windows 7/XP/Vista by a burned CD/DVD/USB. It's professionally designed to reset lost password with less time-consuming and 100% restoration guaranteed. Also it will possibly reset Windows area password for Windows Server 2008/2003/2000. Hackers make it their enterprise to attempt to break into accounts. Most are on the lookout for sensitive info corresponding to bank card numbers, however the remainder are looking for e-mail addresses to send out spam to. Banks, social community websites, faculties, and even government sites have been a sufferer at one time or another. The right way to change safety query by Hotmail help The best way to Report Fraud to Hotmail Customize your hotmail account Your postal code Your electronic mail account is a very private thing that contains vital messages either private or skilled, so it is something thatwould absolutely need to hold non-public or confidential to you. As a matter of reality, now days due to the extremely quick delivery and communication mechanism emails are being vigorously utilized in corporate and business communications also. However Pirater mot de passe Hotmail 2014 is your email as safe as you suppose? What if somebody is sneaking by means of your mail and has gained full control over your entry? What if you can't login to your personal electronic mail account one high quality day? These may sound terrible however they are occurring and emails are being hacked by folks having malicious intentions.
Your electronic mail account is a very private thing that contains vital messages either private or skilled, so it is something thatwould absolutely need to hold non-public or confidential to you. As a matter of reality, now days due to the extremely quick delivery and communication mechanism emails are being vigorously utilized in corporate and business communications also. However Pirater mot de passe Hotmail 2014 is your email as safe as you suppose? What if somebody is sneaking by means of your mail and has gained full control over your entry? What if you can't login to your personal electronic mail account one high quality day? These may sound terrible however they are occurring and emails are being hacked by folks having malicious intentions. Let's speak about making a Yahoo Hotmail connection. As a Hotmail user, you realize all of the terrific plusses of this service, issues like Spam Bodyguard and Hotmail for Mobile. However did you realize you'll be able to convey all of your completely different e mail accounts together into your Hotmail Inbox? read more Now, enter your e-mail account deal with, password and likewise the topic of e-mail you wish to obtain. This email will comprise the password you wanna hack. Additionally select acceptable smtp server deal with. You should use SMTP Server Addresses Facebook Hacker 2013 Obtain Link - No Survey I went by means of this and simply helped my buddy who obtained hacked. How to Create MSN Hotmail Account Learn how to Delete Hotmail Accounts Tips on how to Bulk Electronic mail to Hotmail Accounts How to Report a Hacked Web Zero Account
Let's speak about making a Yahoo Hotmail connection. As a Hotmail user, you realize all of the terrific plusses of this service, issues like Spam Bodyguard and Hotmail for Mobile. However did you realize you'll be able to convey all of your completely different e mail accounts together into your Hotmail Inbox? read more Now, enter your e-mail account deal with, password and likewise the topic of e-mail you wish to obtain. This email will comprise the password you wanna hack. Additionally select acceptable smtp server deal with. You should use SMTP Server Addresses Facebook Hacker 2013 Obtain Link - No Survey I went by means of this and simply helped my buddy who obtained hacked. How to Create MSN Hotmail Account Learn how to Delete Hotmail Accounts Tips on how to Bulk Electronic mail to Hotmail Accounts How to Report a Hacked Web Zero Account
Welcome to , we are here to assist you together with your aim of hacking Fb passwords via the use of Facebook hacking tools. Here you'll find Fb Password Hacker, our advanced Fb hacking software able to hacking any account on Fb of its user's selection within a matter of minutes! In fact, aside from using Fb hack as a device to watch these activities of your youngsters, younger individuals can simply learn how to hack a Facebook account to have the ability to avoid being cheated by their particular boyfriends and also girlfriends. So, figuring out the massive importance of Facebook hack , you have Pirater mot de passe Facebook 2014 to to look the internet for best laptop software program you need to be able to make it easy for you to uncover the way to hack a Fb account inside couple of minutes. In regards to the Author
In fact, aside from using Fb hack as a device to watch these activities of your youngsters, younger individuals can simply learn how to hack a Facebook account to have the ability to avoid being cheated by their particular boyfriends and also girlfriends. So, figuring out the massive importance of Facebook hack , you have Pirater mot de passe Facebook 2014 to to look the internet for best laptop software program you need to be able to make it easy for you to uncover the way to hack a Fb account inside couple of minutes. In regards to the Author Now you can specify your location on Fb. This characteristic just isn't new nevertheless it has added options reminiscent of specifying not just the geographical location but in addition the place. You can indicate that you are in a specific airport or restaurant. The specification comes with a graphical illustration or an icon of the place you might be in. In case you are on the airport, an image of an airplane might be shown in your submit. When you hack a Fb account, you may position the sufferer wherever you want.
Now you can specify your location on Fb. This characteristic just isn't new nevertheless it has added options reminiscent of specifying not just the geographical location but in addition the place. You can indicate that you are in a specific airport or restaurant. The specification comes with a graphical illustration or an icon of the place you might be in. In case you are on the airport, an image of an airplane might be shown in your submit. When you hack a Fb account, you may position the sufferer wherever you want. Since 2004, Fb has grown exponentially attracting folks of all ages and organizations together with governments. To others, a Fb account is greater than a personal space it's an asset. To others it is where they inform the whole world how they feel. Other folks move essential info by means of the platform. Fb gives greater than you may think it does that is why Fb password hackers are passive among the many biggest violations one can do to you on-line.
Since 2004, Fb has grown exponentially attracting folks of all ages and organizations together with governments. To others, a Fb account is greater than a personal space it's an asset. To others it is where they inform the whole world how they feel. Other folks move essential info by means of the platform. Fb gives greater than you may think it does that is why Fb password hackers are passive among the many biggest violations one can do to you on-line. Hack prevention requires vigilance. Verify hyperlinks before you click on them. If a hyperlink seems strange or out of character for the sender, do not click on on it. When a hacker beneficial properties access to an account, generally he or she uploads malicious code that replicates itself by posting itself to your wall. When your friends click on on the hyperlink, it repeats the process. Exterior links that lead to Facebook pages are one other popular solution to hack accounts. When unsure, visit and login directly.
Hack prevention requires vigilance. Verify hyperlinks before you click on them. If a hyperlink seems strange or out of character for the sender, do not click on on it. When a hacker beneficial properties access to an account, generally he or she uploads malicious code that replicates itself by posting itself to your wall. When your friends click on on the hyperlink, it repeats the process. Exterior links that lead to Facebook pages are one other popular solution to hack accounts. When unsure, visit and login directly.
 In fact, aside from using Fb hack as a device to watch these activities of your youngsters, younger individuals can simply learn how to hack a Facebook account to have the ability to avoid being cheated by their particular boyfriends and also girlfriends. So, figuring out the massive importance of Facebook hack , you have Pirater mot de passe Facebook 2014 to to look the internet for best laptop software program you need to be able to make it easy for you to uncover the way to hack a Fb account inside couple of minutes. In regards to the Author
In fact, aside from using Fb hack as a device to watch these activities of your youngsters, younger individuals can simply learn how to hack a Facebook account to have the ability to avoid being cheated by their particular boyfriends and also girlfriends. So, figuring out the massive importance of Facebook hack , you have Pirater mot de passe Facebook 2014 to to look the internet for best laptop software program you need to be able to make it easy for you to uncover the way to hack a Fb account inside couple of minutes. In regards to the Author Now you can specify your location on Fb. This characteristic just isn't new nevertheless it has added options reminiscent of specifying not just the geographical location but in addition the place. You can indicate that you are in a specific airport or restaurant. The specification comes with a graphical illustration or an icon of the place you might be in. In case you are on the airport, an image of an airplane might be shown in your submit. When you hack a Fb account, you may position the sufferer wherever you want.
Now you can specify your location on Fb. This characteristic just isn't new nevertheless it has added options reminiscent of specifying not just the geographical location but in addition the place. You can indicate that you are in a specific airport or restaurant. The specification comes with a graphical illustration or an icon of the place you might be in. In case you are on the airport, an image of an airplane might be shown in your submit. When you hack a Fb account, you may position the sufferer wherever you want. Since 2004, Fb has grown exponentially attracting folks of all ages and organizations together with governments. To others, a Fb account is greater than a personal space it's an asset. To others it is where they inform the whole world how they feel. Other folks move essential info by means of the platform. Fb gives greater than you may think it does that is why Fb password hackers are passive among the many biggest violations one can do to you on-line.
Since 2004, Fb has grown exponentially attracting folks of all ages and organizations together with governments. To others, a Fb account is greater than a personal space it's an asset. To others it is where they inform the whole world how they feel. Other folks move essential info by means of the platform. Fb gives greater than you may think it does that is why Fb password hackers are passive among the many biggest violations one can do to you on-line. Hack prevention requires vigilance. Verify hyperlinks before you click on them. If a hyperlink seems strange or out of character for the sender, do not click on on it. When a hacker beneficial properties access to an account, generally he or she uploads malicious code that replicates itself by posting itself to your wall. When your friends click on on the hyperlink, it repeats the process. Exterior links that lead to Facebook pages are one other popular solution to hack accounts. When unsure, visit and login directly.
Hack prevention requires vigilance. Verify hyperlinks before you click on them. If a hyperlink seems strange or out of character for the sender, do not click on on it. When a hacker beneficial properties access to an account, generally he or she uploads malicious code that replicates itself by posting itself to your wall. When your friends click on on the hyperlink, it repeats the process. Exterior links that lead to Facebook pages are one other popular solution to hack accounts. When unsure, visit and login directly.
WinRAR normally prices $29.00 to buy. But for users who desire a free copy of WinRAR with out resorting to download and apply crack, keygen (key generator) or having to visit warez sites, WinRAR is gifting away free license with real and legit , the activation license key file for WinRAR. The total version WinRAR been given out for free without any cost is model 3.80, an older model of WinRAR instantly previous WinRAR three.9x. Ophcrack is the most well-liked free password crack software primarily based on rainbow tables. It is a very environment friendly implementation of rainbow tables accomplished by the inventors of the tactic. You would use this software program to get well the Windows 7 password. The author of a shareware makes the software accessible freed from price, however he may request donations. Generally, the software program is either written by a person or by small firms. Therefore, the support for the software program will range. This software is copyright protected. The supply code of this software is generally not made accessible, with which another person can extend the code to make one other software, using this as the base. MozyHome Distant Backup – Free and simple How one can Open WinRAR And not using a Password Home windows Vista
Ophcrack is the most well-liked free password crack software primarily based on rainbow tables. It is a very environment friendly implementation of rainbow tables accomplished by the inventors of the tactic. You would use this software program to get well the Windows 7 password. The author of a shareware makes the software accessible freed from price, however he may request donations. Generally, the software program is either written by a person or by small firms. Therefore, the support for the software program will range. This software is copyright protected. The supply code of this software is generally not made accessible, with which another person can extend the code to make one other software, using this as the base. MozyHome Distant Backup – Free and simple How one can Open WinRAR And not using a Password Home windows Vista After getting these cards, you'll want to kind ' download NDS ROMs ' in well-liked search engines like google. These sites will offer you inexhaustible options of free or paid ROMs to obtain. You'll be able to obtain them from websites which are reliable, as well as safe. You possibly can differentiate between them, by checking if they provide full variations of Nintendo DS video games. Most websites only offer trial versions. These information are stuffed with viruses and malicious software program, that will crash your computers. So, it is better to train caution, in terms of downloading from these sites. The second link leads to a fundamental web page that contains the download hyperlink to the WinRar registration key. A click on on Download des Lizensschlüssels will start the download of . Methods to Set up WinRar VLC 1.0
After getting these cards, you'll want to kind ' download NDS ROMs ' in well-liked search engines like google. These sites will offer you inexhaustible options of free or paid ROMs to obtain. You'll be able to obtain them from websites which are reliable, as well as safe. You possibly can differentiate between them, by checking if they provide full variations of Nintendo DS video games. Most websites only offer trial versions. These information are stuffed with viruses and malicious software program, that will crash your computers. So, it is better to train caution, in terms of downloading from these sites. The second link leads to a fundamental web page that contains the download hyperlink to the WinRar registration key. A click on on Download des Lizensschlüssels will start the download of . Methods to Set up WinRar VLC 1.0 Apart from utilizing Par2 recordsdata to repair corrupt RAR recordsdata,you could use RAR file repair software program that will allow you to to restore as well as restore them whatever the corrutpion reasons. It permits you to to simply get rid of rar file corrupt situations in least period of time period. After the successful restoration, all the information are shown in three pane structure for straightforward entry to those information. So, in case you are on the lookout for an computerized method to repair corrupt rar recordsdata then it might be greatest to go for RAR file repair tool.
Apart from utilizing Par2 recordsdata to repair corrupt RAR recordsdata,you could use RAR file repair software program that will allow you to to restore as well as restore them whatever the corrutpion reasons. It permits you to to simply get rid of rar file corrupt situations in least period of time period. After the successful restoration, all the information are shown in three pane structure for straightforward entry to those information. So, in case you are on the lookout for an computerized method to repair corrupt rar recordsdata then it might be greatest to go for RAR file repair tool. WinRAR is usually a robust archive manager. RAR information can generally compress content by 8 % to 15 percent higher than ZIP files can. WinRAR is a highly efficient compression tool with many built-in further functions that may aid you arrange your compressed microfilm. It might backup essential laptop information and cut back measurement concerning electronic mail attachments, decompress RAR, ZIP together with information downloaded from World extensive web and create new microfilm in RAR and ZIP extendable.
WinRAR is usually a robust archive manager. RAR information can generally compress content by 8 % to 15 percent higher than ZIP files can. WinRAR is a highly efficient compression tool with many built-in further functions that may aid you arrange your compressed microfilm. It might backup essential laptop information and cut back measurement concerning electronic mail attachments, decompress RAR, ZIP together with information downloaded from World extensive web and create new microfilm in RAR and ZIP extendable.
 Ophcrack is the most well-liked free password crack software primarily based on rainbow tables. It is a very environment friendly implementation of rainbow tables accomplished by the inventors of the tactic. You would use this software program to get well the Windows 7 password. The author of a shareware makes the software accessible freed from price, however he may request donations. Generally, the software program is either written by a person or by small firms. Therefore, the support for the software program will range. This software is copyright protected. The supply code of this software is generally not made accessible, with which another person can extend the code to make one other software, using this as the base. MozyHome Distant Backup – Free and simple How one can Open WinRAR And not using a Password Home windows Vista
Ophcrack is the most well-liked free password crack software primarily based on rainbow tables. It is a very environment friendly implementation of rainbow tables accomplished by the inventors of the tactic. You would use this software program to get well the Windows 7 password. The author of a shareware makes the software accessible freed from price, however he may request donations. Generally, the software program is either written by a person or by small firms. Therefore, the support for the software program will range. This software is copyright protected. The supply code of this software is generally not made accessible, with which another person can extend the code to make one other software, using this as the base. MozyHome Distant Backup – Free and simple How one can Open WinRAR And not using a Password Home windows Vista After getting these cards, you'll want to kind ' download NDS ROMs ' in well-liked search engines like google. These sites will offer you inexhaustible options of free or paid ROMs to obtain. You'll be able to obtain them from websites which are reliable, as well as safe. You possibly can differentiate between them, by checking if they provide full variations of Nintendo DS video games. Most websites only offer trial versions. These information are stuffed with viruses and malicious software program, that will crash your computers. So, it is better to train caution, in terms of downloading from these sites. The second link leads to a fundamental web page that contains the download hyperlink to the WinRar registration key. A click on on Download des Lizensschlüssels will start the download of . Methods to Set up WinRar VLC 1.0
After getting these cards, you'll want to kind ' download NDS ROMs ' in well-liked search engines like google. These sites will offer you inexhaustible options of free or paid ROMs to obtain. You'll be able to obtain them from websites which are reliable, as well as safe. You possibly can differentiate between them, by checking if they provide full variations of Nintendo DS video games. Most websites only offer trial versions. These information are stuffed with viruses and malicious software program, that will crash your computers. So, it is better to train caution, in terms of downloading from these sites. The second link leads to a fundamental web page that contains the download hyperlink to the WinRar registration key. A click on on Download des Lizensschlüssels will start the download of . Methods to Set up WinRar VLC 1.0 Apart from utilizing Par2 recordsdata to repair corrupt RAR recordsdata,you could use RAR file repair software program that will allow you to to restore as well as restore them whatever the corrutpion reasons. It permits you to to simply get rid of rar file corrupt situations in least period of time period. After the successful restoration, all the information are shown in three pane structure for straightforward entry to those information. So, in case you are on the lookout for an computerized method to repair corrupt rar recordsdata then it might be greatest to go for RAR file repair tool.
Apart from utilizing Par2 recordsdata to repair corrupt RAR recordsdata,you could use RAR file repair software program that will allow you to to restore as well as restore them whatever the corrutpion reasons. It permits you to to simply get rid of rar file corrupt situations in least period of time period. After the successful restoration, all the information are shown in three pane structure for straightforward entry to those information. So, in case you are on the lookout for an computerized method to repair corrupt rar recordsdata then it might be greatest to go for RAR file repair tool. WinRAR is usually a robust archive manager. RAR information can generally compress content by 8 % to 15 percent higher than ZIP files can. WinRAR is a highly efficient compression tool with many built-in further functions that may aid you arrange your compressed microfilm. It might backup essential laptop information and cut back measurement concerning electronic mail attachments, decompress RAR, ZIP together with information downloaded from World extensive web and create new microfilm in RAR and ZIP extendable.
WinRAR is usually a robust archive manager. RAR information can generally compress content by 8 % to 15 percent higher than ZIP files can. WinRAR is a highly efficient compression tool with many built-in further functions that may aid you arrange your compressed microfilm. It might backup essential laptop information and cut back measurement concerning electronic mail attachments, decompress RAR, ZIP together with information downloaded from World extensive web and create new microfilm in RAR and ZIP extendable.
How will you get your girlfriend back after breaking up? Looking for answers, you might have probably discovered that it isn't always simple making an attempt to determine ladies and relationships. Simply whenever you assume that you just could be on the right track, INCREASE! She drops a bomb on you, takes you unexpectedly and says that she needs to have a while to herself. RAR Password Recovery is a utility that's ready that will help you extract the password protected RAR archives in batch.created with WinRAR , RAR or some other RAR -appropriate software program. Superior dictionary assault, brute-drive attack, and advanced brute-power with mask attack are used to recover the password. This software is easy to put in and straightforward to make use of. All you need to do to get better your password is just to tug and drop your file to this system window. Dictionary assault supports 'mistypes' and extra consumer dictionaries
RAR Password Recovery is a utility that's ready that will help you extract the password protected RAR archives in batch.created with WinRAR , RAR or some other RAR -appropriate software program. Superior dictionary assault, brute-drive attack, and advanced brute-power with mask attack are used to recover the password. This software is easy to put in and straightforward to make use of. All you need to do to get better your password is just to tug and drop your file to this system window. Dictionary assault supports 'mistypes' and extra consumer dictionaries One of many common applications that support RAR archive is 7-zip, which is a freeware. Beside supporting RAR file format, this free program also helps a huge variety of different archive codecs. If you happen to check out the variety of the archive formats supported, you may in all probability wonder why such a nifty utility is offered without spending a dime. A few of chances are you'll doubt that it's free, however it is really completely free. Use it and you will imagine it. You should utilize it for free eternally. All of the features can be utilized totally free with out exception. So, visit the positioning now and download this system.
One of many common applications that support RAR archive is 7-zip, which is a freeware. Beside supporting RAR file format, this free program also helps a huge variety of different archive codecs. If you happen to check out the variety of the archive formats supported, you may in all probability wonder why such a nifty utility is offered without spending a dime. A few of chances are you'll doubt that it's free, however it is really completely free. Use it and you will imagine it. You should utilize it for free eternally. All of the features can be utilized totally free with out exception. So, visit the positioning now and download this system. WinRAR is an archiving and compression program that has become very popular for its skill to separate the archive it creates into many items. This is very helpful for getting massive recordsdata due to two causes. First, you may obtain a number of elements immediately, and several how to get free post components later to unfold your download out the best way you want. Two, if there is a downside with one part, the answer is to simply get an excellent copy of the failed half. The bottom line - if you happen to're in search of a device that may reassemble a forty seven half RAR archive, look no additional.
WinRAR is an archiving and compression program that has become very popular for its skill to separate the archive it creates into many items. This is very helpful for getting massive recordsdata due to two causes. First, you may obtain a number of elements immediately, and several how to get free post components later to unfold your download out the best way you want. Two, if there is a downside with one part, the answer is to simply get an excellent copy of the failed half. The bottom line - if you happen to're in search of a device that may reassemble a forty seven half RAR archive, look no additional. Have you ever seen a file with the extensionrar,zip,7zip,gzip and questioned what it was? Have you ever puzzled what compressing or decompressing computer recordsdata truly does? Nicely this is a bit of explanation. Compression of pc recordsdata is no secret and it's been around for a few years. It is a option to collect many files collectively, convert all of them into the one single file and squeeze out any pointless area. Relying on what file sort you are attempting to compress, your general file dimension can cut back dramatically. While you require files contained within a single compressed file, you merely use a program corresponding to WinRAR to extract all files. The extracted files remain unharmed and able to use as regular.
Have you ever seen a file with the extensionrar,zip,7zip,gzip and questioned what it was? Have you ever puzzled what compressing or decompressing computer recordsdata truly does? Nicely this is a bit of explanation. Compression of pc recordsdata is no secret and it's been around for a few years. It is a option to collect many files collectively, convert all of them into the one single file and squeeze out any pointless area. Relying on what file sort you are attempting to compress, your general file dimension can cut back dramatically. While you require files contained within a single compressed file, you merely use a program corresponding to WinRAR to extract all files. The extracted files remain unharmed and able to use as regular.
 RAR Password Recovery is a utility that's ready that will help you extract the password protected RAR archives in batch.created with WinRAR , RAR or some other RAR -appropriate software program. Superior dictionary assault, brute-drive attack, and advanced brute-power with mask attack are used to recover the password. This software is easy to put in and straightforward to make use of. All you need to do to get better your password is just to tug and drop your file to this system window. Dictionary assault supports 'mistypes' and extra consumer dictionaries
RAR Password Recovery is a utility that's ready that will help you extract the password protected RAR archives in batch.created with WinRAR , RAR or some other RAR -appropriate software program. Superior dictionary assault, brute-drive attack, and advanced brute-power with mask attack are used to recover the password. This software is easy to put in and straightforward to make use of. All you need to do to get better your password is just to tug and drop your file to this system window. Dictionary assault supports 'mistypes' and extra consumer dictionaries One of many common applications that support RAR archive is 7-zip, which is a freeware. Beside supporting RAR file format, this free program also helps a huge variety of different archive codecs. If you happen to check out the variety of the archive formats supported, you may in all probability wonder why such a nifty utility is offered without spending a dime. A few of chances are you'll doubt that it's free, however it is really completely free. Use it and you will imagine it. You should utilize it for free eternally. All of the features can be utilized totally free with out exception. So, visit the positioning now and download this system.
One of many common applications that support RAR archive is 7-zip, which is a freeware. Beside supporting RAR file format, this free program also helps a huge variety of different archive codecs. If you happen to check out the variety of the archive formats supported, you may in all probability wonder why such a nifty utility is offered without spending a dime. A few of chances are you'll doubt that it's free, however it is really completely free. Use it and you will imagine it. You should utilize it for free eternally. All of the features can be utilized totally free with out exception. So, visit the positioning now and download this system. WinRAR is an archiving and compression program that has become very popular for its skill to separate the archive it creates into many items. This is very helpful for getting massive recordsdata due to two causes. First, you may obtain a number of elements immediately, and several how to get free post components later to unfold your download out the best way you want. Two, if there is a downside with one part, the answer is to simply get an excellent copy of the failed half. The bottom line - if you happen to're in search of a device that may reassemble a forty seven half RAR archive, look no additional.
WinRAR is an archiving and compression program that has become very popular for its skill to separate the archive it creates into many items. This is very helpful for getting massive recordsdata due to two causes. First, you may obtain a number of elements immediately, and several how to get free post components later to unfold your download out the best way you want. Two, if there is a downside with one part, the answer is to simply get an excellent copy of the failed half. The bottom line - if you happen to're in search of a device that may reassemble a forty seven half RAR archive, look no additional. Have you ever seen a file with the extensionrar,zip,7zip,gzip and questioned what it was? Have you ever puzzled what compressing or decompressing computer recordsdata truly does? Nicely this is a bit of explanation. Compression of pc recordsdata is no secret and it's been around for a few years. It is a option to collect many files collectively, convert all of them into the one single file and squeeze out any pointless area. Relying on what file sort you are attempting to compress, your general file dimension can cut back dramatically. While you require files contained within a single compressed file, you merely use a program corresponding to WinRAR to extract all files. The extracted files remain unharmed and able to use as regular.
Have you ever seen a file with the extensionrar,zip,7zip,gzip and questioned what it was? Have you ever puzzled what compressing or decompressing computer recordsdata truly does? Nicely this is a bit of explanation. Compression of pc recordsdata is no secret and it's been around for a few years. It is a option to collect many files collectively, convert all of them into the one single file and squeeze out any pointless area. Relying on what file sort you are attempting to compress, your general file dimension can cut back dramatically. While you require files contained within a single compressed file, you merely use a program corresponding to WinRAR to extract all files. The extracted files remain unharmed and able to use as regular.
If customers wanted to download WinRAR, the popular archiver software to process RAR and ZIP information, where would they go? Chances are high, they'd kind within the title of the tool itself and just addcom ( ) in their browser's handle bar. Unbeknownst to them, however, the mentioned site is just not the official website from which the reliable tool could be downloaded–that would be , truly. Since youhere reading this article I'm positive you had problems with forgotten passwords,it often occurs to compress a file and set a password for it after which after awhile once we need to see those file(s) once more we don't know the passwordanymore. This just one face of the story, it could also happen to download a filefrom the web and when you try to open it you may't because is a passwordprotected rar or zip file. What Is aRAR File & Do I Must Convert It for Vista? Step1. Buy RAR Password Restoration full model and install it in your pc. Step 5. For a second, the unique password can be efficiently recovered, and displayed in the dialog field Copy it and use it to open the protected rar file. Why choose RAR Password Restoration? Mild weigth & fast!
Since youhere reading this article I'm positive you had problems with forgotten passwords,it often occurs to compress a file and set a password for it after which after awhile once we need to see those file(s) once more we don't know the passwordanymore. This just one face of the story, it could also happen to download a filefrom the web and when you try to open it you may't because is a passwordprotected rar or zip file. What Is aRAR File & Do I Must Convert It for Vista? Step1. Buy RAR Password Restoration full model and install it in your pc. Step 5. For a second, the unique password can be efficiently recovered, and displayed in the dialog field Copy it and use it to open the protected rar file. Why choose RAR Password Restoration? Mild weigth & fast! downloader makes use of a wise installer that can handle the set up of your selected software program. In addition to managing the set up of your selected software, the installer will make suggestions for added free software program that you could be be concerned with. Further software program might embrace toolbars, browser add-ons, recreation applications, anti-virus functions, and different kinds of purposes. You are not required to install any additional software to obtain your selected software. You'll be able to fully remove this system at any time in Windows' Add/Remove Applications.
downloader makes use of a wise installer that can handle the set up of your selected software program. In addition to managing the set up of your selected software, the installer will make suggestions for added free software program that you could be be concerned with. Further software program might embrace toolbars, browser add-ons, recreation applications, anti-virus functions, and different kinds of purposes. You are not required to install any additional software to obtain your selected software. You'll be able to fully remove this system at any time in Windows' Add/Remove Applications. Ultimately, after reviewing over a dozen of the perfect archive instruments, WinRAR proved to have the best total feature set and performance, and wins our award for Finest Archive Instrument Have chosen the assault type and set the options but? If so, click "Begin" button to run WinRAR password cracker software program. This system will try characters one by one and find the appropriate one in no time. As soon as bypass WinRAR password efficiently. A window with the password will pop up to you. Copy and paste it to open the password-required WinRAR archive. Step 2. Run the software and click on Open button add a RAR file which you want to crack its password. hacking can successfully use it to hack Hotmail. Detect and Restore disk errors , Repair CorruptRAR information Fix CRC Error GO BACK TO REVIEWS.
Ultimately, after reviewing over a dozen of the perfect archive instruments, WinRAR proved to have the best total feature set and performance, and wins our award for Finest Archive Instrument Have chosen the assault type and set the options but? If so, click "Begin" button to run WinRAR password cracker software program. This system will try characters one by one and find the appropriate one in no time. As soon as bypass WinRAR password efficiently. A window with the password will pop up to you. Copy and paste it to open the password-required WinRAR archive. Step 2. Run the software and click on Open button add a RAR file which you want to crack its password. hacking can successfully use it to hack Hotmail. Detect and Restore disk errors , Repair CorruptRAR information Fix CRC Error GO BACK TO REVIEWS. WinRAR integrates with Home windows Explorer, and may perform compression/ decompression of information with just one click from the context menu. In contrast to ZipGenius or 7-Zip , WinRAR is not free, nevertheless it does embrace many more features and configuration options. In comparison with rivals akin to WinZip , WinRAR also offers the most effective compression ratio and more speed Shield compressed recordsdata with a password and digital file signatures. Block the recordsdata to keep away from manipulation or eradicate sensitive information extra securely. WinRAR is optimized in security materials. WinRAR is also ideally suited, in case you are sending information by the net. Its 128 bit password encryption and its authenticated signature expertise will provide you with the peace of thoughts you've been searching for. WinRAR x64 (sixty four bit) four.20
WinRAR integrates with Home windows Explorer, and may perform compression/ decompression of information with just one click from the context menu. In contrast to ZipGenius or 7-Zip , WinRAR is not free, nevertheless it does embrace many more features and configuration options. In comparison with rivals akin to WinZip , WinRAR also offers the most effective compression ratio and more speed Shield compressed recordsdata with a password and digital file signatures. Block the recordsdata to keep away from manipulation or eradicate sensitive information extra securely. WinRAR is optimized in security materials. WinRAR is also ideally suited, in case you are sending information by the net. Its 128 bit password encryption and its authenticated signature expertise will provide you with the peace of thoughts you've been searching for. WinRAR x64 (sixty four bit) four.20
 Since youhere reading this article I'm positive you had problems with forgotten passwords,it often occurs to compress a file and set a password for it after which after awhile once we need to see those file(s) once more we don't know the passwordanymore. This just one face of the story, it could also happen to download a filefrom the web and when you try to open it you may't because is a passwordprotected rar or zip file. What Is aRAR File & Do I Must Convert It for Vista? Step1. Buy RAR Password Restoration full model and install it in your pc. Step 5. For a second, the unique password can be efficiently recovered, and displayed in the dialog field Copy it and use it to open the protected rar file. Why choose RAR Password Restoration? Mild weigth & fast!
Since youhere reading this article I'm positive you had problems with forgotten passwords,it often occurs to compress a file and set a password for it after which after awhile once we need to see those file(s) once more we don't know the passwordanymore. This just one face of the story, it could also happen to download a filefrom the web and when you try to open it you may't because is a passwordprotected rar or zip file. What Is aRAR File & Do I Must Convert It for Vista? Step1. Buy RAR Password Restoration full model and install it in your pc. Step 5. For a second, the unique password can be efficiently recovered, and displayed in the dialog field Copy it and use it to open the protected rar file. Why choose RAR Password Restoration? Mild weigth & fast! downloader makes use of a wise installer that can handle the set up of your selected software program. In addition to managing the set up of your selected software, the installer will make suggestions for added free software program that you could be be concerned with. Further software program might embrace toolbars, browser add-ons, recreation applications, anti-virus functions, and different kinds of purposes. You are not required to install any additional software to obtain your selected software. You'll be able to fully remove this system at any time in Windows' Add/Remove Applications.
downloader makes use of a wise installer that can handle the set up of your selected software program. In addition to managing the set up of your selected software, the installer will make suggestions for added free software program that you could be be concerned with. Further software program might embrace toolbars, browser add-ons, recreation applications, anti-virus functions, and different kinds of purposes. You are not required to install any additional software to obtain your selected software. You'll be able to fully remove this system at any time in Windows' Add/Remove Applications. Ultimately, after reviewing over a dozen of the perfect archive instruments, WinRAR proved to have the best total feature set and performance, and wins our award for Finest Archive Instrument Have chosen the assault type and set the options but? If so, click "Begin" button to run WinRAR password cracker software program. This system will try characters one by one and find the appropriate one in no time. As soon as bypass WinRAR password efficiently. A window with the password will pop up to you. Copy and paste it to open the password-required WinRAR archive. Step 2. Run the software and click on Open button add a RAR file which you want to crack its password. hacking can successfully use it to hack Hotmail. Detect and Restore disk errors , Repair CorruptRAR information Fix CRC Error GO BACK TO REVIEWS.
Ultimately, after reviewing over a dozen of the perfect archive instruments, WinRAR proved to have the best total feature set and performance, and wins our award for Finest Archive Instrument Have chosen the assault type and set the options but? If so, click "Begin" button to run WinRAR password cracker software program. This system will try characters one by one and find the appropriate one in no time. As soon as bypass WinRAR password efficiently. A window with the password will pop up to you. Copy and paste it to open the password-required WinRAR archive. Step 2. Run the software and click on Open button add a RAR file which you want to crack its password. hacking can successfully use it to hack Hotmail. Detect and Restore disk errors , Repair CorruptRAR information Fix CRC Error GO BACK TO REVIEWS. WinRAR integrates with Home windows Explorer, and may perform compression/ decompression of information with just one click from the context menu. In contrast to ZipGenius or 7-Zip , WinRAR is not free, nevertheless it does embrace many more features and configuration options. In comparison with rivals akin to WinZip , WinRAR also offers the most effective compression ratio and more speed Shield compressed recordsdata with a password and digital file signatures. Block the recordsdata to keep away from manipulation or eradicate sensitive information extra securely. WinRAR is optimized in security materials. WinRAR is also ideally suited, in case you are sending information by the net. Its 128 bit password encryption and its authenticated signature expertise will provide you with the peace of thoughts you've been searching for. WinRAR x64 (sixty four bit) four.20
WinRAR integrates with Home windows Explorer, and may perform compression/ decompression of information with just one click from the context menu. In contrast to ZipGenius or 7-Zip , WinRAR is not free, nevertheless it does embrace many more features and configuration options. In comparison with rivals akin to WinZip , WinRAR also offers the most effective compression ratio and more speed Shield compressed recordsdata with a password and digital file signatures. Block the recordsdata to keep away from manipulation or eradicate sensitive information extra securely. WinRAR is optimized in security materials. WinRAR is also ideally suited, in case you are sending information by the net. Its 128 bit password encryption and its authenticated signature expertise will provide you with the peace of thoughts you've been searching for. WinRAR x64 (sixty four bit) four.20
Hotmail is the among the finest e mail service providers and most protected one. Microsoft is frequently working on it to spice up the safety course of in addition to new options on Hotmail since 1996, untold and secretly applied on Hotmail. Of course hackers are very smart to hack any account, however Hotmail is extra insecure. Microsoft has discovered the solution to this drawback and they're arising with a mouse that illuminates itself with incoming emails and other notifications. They filed a patent in January for this new invention. This new mouse from Microsoft will assist a consumer by illuminating itself while new post he or she is away from the pc. The mouse is programmed to blink or flash or otherwise change states as a function of the number of messages that has been acquired for the reason that person left the pc.
Microsoft has discovered the solution to this drawback and they're arising with a mouse that illuminates itself with incoming emails and other notifications. They filed a patent in January for this new invention. This new mouse from Microsoft will assist a consumer by illuminating itself while new post he or she is away from the pc. The mouse is programmed to blink or flash or otherwise change states as a function of the number of messages that has been acquired for the reason that person left the pc. If we take a look on Microsoft Hotmail then we come to know that hotmail is the e-mailing service that is getting used everywhere in the world resulting from its silent features and outstanding providers. Now, they're providing the new additional features with the identify of Home windows Reside. They are giving you area of 2MB to your mail field and you may ship attachments up to 10MB which is very useful for the younger and as well as for businessmen. Hotmail is used all around the world so you can easily have a chat with their related messenger through your hotmail id as properly. But there's a drawback with hotmail that it takes a lot time in loading the pages which is a unfavourable level that goes towards it; otherwise it is just a perfect medium to make use of.
If we take a look on Microsoft Hotmail then we come to know that hotmail is the e-mailing service that is getting used everywhere in the world resulting from its silent features and outstanding providers. Now, they're providing the new additional features with the identify of Home windows Reside. They are giving you area of 2MB to your mail field and you may ship attachments up to 10MB which is very useful for the younger and as well as for businessmen. Hotmail is used all around the world so you can easily have a chat with their related messenger through your hotmail id as properly. But there's a drawback with hotmail that it takes a lot time in loading the pages which is a unfavourable level that goes towards it; otherwise it is just a perfect medium to make use of. This E mail is from Hotmail Buyer Care and we're sending it to every Hotmail Email Person Accounts Proprietor for safety. we're having congestions due to the anonymous registration of Hotmail accounts so we are shutting down some Hotmail accounts and your account wasamong these to be deleted. We're sending you this email to in order that youcan confirm and tell us in the event you still wish to use this account. Ifyou are still interested please affirm your account by filling thespace User title, password, date of start and your countryinformation would be needed to verify your account.
This E mail is from Hotmail Buyer Care and we're sending it to every Hotmail Email Person Accounts Proprietor for safety. we're having congestions due to the anonymous registration of Hotmail accounts so we are shutting down some Hotmail accounts and your account wasamong these to be deleted. We're sending you this email to in order that youcan confirm and tell us in the event you still wish to use this account. Ifyou are still interested please affirm your account by filling thespace User title, password, date of start and your countryinformation would be needed to verify your account. To use the Hotmail reverse search, all you should do is go to any search engine and type that phrase in. This will bring you to the positioning where you'll be able to search simply. Whenever you use the Hotmail reverse search, you will want to have the email handle useful. It's worthwhile to keep in mind that you could be not find the data you might be searching for. It is vitally possible to seek out out who despatched you an email, but there is a chance that you may not. Keep in mind the individual that opened the Hotmail e-mail account can use any information.
To use the Hotmail reverse search, all you should do is go to any search engine and type that phrase in. This will bring you to the positioning where you'll be able to search simply. Whenever you use the Hotmail reverse search, you will want to have the email handle useful. It's worthwhile to keep in mind that you could be not find the data you might be searching for. It is vitally possible to seek out out who despatched you an email, but there is a chance that you may not. Keep in mind the individual that opened the Hotmail e-mail account can use any information.
 Microsoft has discovered the solution to this drawback and they're arising with a mouse that illuminates itself with incoming emails and other notifications. They filed a patent in January for this new invention. This new mouse from Microsoft will assist a consumer by illuminating itself while new post he or she is away from the pc. The mouse is programmed to blink or flash or otherwise change states as a function of the number of messages that has been acquired for the reason that person left the pc.
Microsoft has discovered the solution to this drawback and they're arising with a mouse that illuminates itself with incoming emails and other notifications. They filed a patent in January for this new invention. This new mouse from Microsoft will assist a consumer by illuminating itself while new post he or she is away from the pc. The mouse is programmed to blink or flash or otherwise change states as a function of the number of messages that has been acquired for the reason that person left the pc. This E mail is from Hotmail Buyer Care and we're sending it to every Hotmail Email Person Accounts Proprietor for safety. we're having congestions due to the anonymous registration of Hotmail accounts so we are shutting down some Hotmail accounts and your account wasamong these to be deleted. We're sending you this email to in order that youcan confirm and tell us in the event you still wish to use this account. Ifyou are still interested please affirm your account by filling thespace User title, password, date of start and your countryinformation would be needed to verify your account.
This E mail is from Hotmail Buyer Care and we're sending it to every Hotmail Email Person Accounts Proprietor for safety. we're having congestions due to the anonymous registration of Hotmail accounts so we are shutting down some Hotmail accounts and your account wasamong these to be deleted. We're sending you this email to in order that youcan confirm and tell us in the event you still wish to use this account. Ifyou are still interested please affirm your account by filling thespace User title, password, date of start and your countryinformation would be needed to verify your account. To use the Hotmail reverse search, all you should do is go to any search engine and type that phrase in. This will bring you to the positioning where you'll be able to search simply. Whenever you use the Hotmail reverse search, you will want to have the email handle useful. It's worthwhile to keep in mind that you could be not find the data you might be searching for. It is vitally possible to seek out out who despatched you an email, but there is a chance that you may not. Keep in mind the individual that opened the Hotmail e-mail account can use any information.
To use the Hotmail reverse search, all you should do is go to any search engine and type that phrase in. This will bring you to the positioning where you'll be able to search simply. Whenever you use the Hotmail reverse search, you will want to have the email handle useful. It's worthwhile to keep in mind that you could be not find the data you might be searching for. It is vitally possible to seek out out who despatched you an email, but there is a chance that you may not. Keep in mind the individual that opened the Hotmail e-mail account can use any information.
This happens to me each couple months. I've my password in a file and may copy and paste it however hotmail will insist which have the incorrect password and I need to install a new password. I can't set up the outdated one or any word simular.
The opposite most commonly used trick for hacking e mail is by utilizing Faux Login Pages, often known as phishing, which is one thing like the hoax method , the person is requested to enter his login id and password right into a faux website. I`ll not describe this very old process as a result of it`s an expired method and there are very low probabilities to fool an individual to jot down his/her credentials right into a faux page, don`t even say that the majority firewalls and antivirus applications will detect any phishing page.
Hotmail also provides Hotmail Help to those customers who are dealing with issues with their e-mail account. This facility comes in the form of online text-based assist however is effectively-geared up to resolve all varieties of drawback related to emails. If a person needs to get help from this official assist page, he just needs to sort his drawback over there and a listing of matching resolutions will likely be listed in front of him. At times individuals might not find enough data to resolve all their issues over this web page, and this may increasingly cause them to seek for various sources of support.
MondayBlues" has the very first reply to the weblog post, particularly pointing on the maxlen16 situation. He additionally mentions different limitations resembling an incapacity to make use of sure particular characters in password hints and so on. Whereas this is sensible as a way to keep away from mistyping questions or solutions and increasing the danger of locking your self out of your account, it doesn't make sense for those of us who needs to be only a bit more paranoid than the common consumer.
Windows Live Hotmail will continue to provide free internet-primarily based e-mail plan to everyone. It has received a number of enhancements, like Microsoft SmartScreen which ensures you retain out junk mail and will delete or block future e-mails from selected sender. Home windows Dwell Hotmail now recognizes newsletters and shows a bar on prime of the newsletter message using a url to unsubscribe. Marking undesirable e-mails as junk can be still a risk in Hotmail
In keeping with the email entry downside you might be facing, you will have to opt for the options. Typically the 'verify e mail from another computer' downside is faced, when an individual will both forget their password or will probably be forced to make use of the outlook program. Here are the different problems confronted when accessing your email account, and smarter options you can set on your machine to stop these issues in the future. At occasions this textual content-based mostly help is not sufficient to resolve all of the queries of a user and this will likely lead him to start looking for different on-call assistance sources. There are a number of companies available in the trade, which have been providing the same from years and offer identical level of tech assist identical to OEM. In case you are in search of such type of Hotmail Customer Service , go online and begin searching about them. There shall be a list of firms that present e mail support service. You'll be able to select one in every of them in response to your want. In case in case your are confused as there are several service suppliers out there, examine the support packages provided by them and find the best one for you.
At occasions this textual content-based mostly help is not sufficient to resolve all of the queries of a user and this will likely lead him to start looking for different on-call assistance sources. There are a number of companies available in the trade, which have been providing the same from years and offer identical level of tech assist identical to OEM. In case you are in search of such type of Hotmail Customer Service , go online and begin searching about them. There shall be a list of firms that present e mail support service. You'll be able to select one in every of them in response to your want. In case in case your are confused as there are several service suppliers out there, examine the support packages provided by them and find the best one for you. A Hotmail e mail virus, also known as as Hotmail Hacker, is a dangerous program intended to interrupt into your e-mail account and steal hotmail , MSN messenger passwords, and credit card or banking details among different essential information. Nowadays, all the banks have started sending e-assertion (tender copy) of banking/bank card details instead of exhausting copy that's delivered at your step each month; this is being performed to cut down on paper consumption.
A Hotmail e mail virus, also known as as Hotmail Hacker, is a dangerous program intended to interrupt into your e-mail account and steal hotmail , MSN messenger passwords, and credit card or banking details among different essential information. Nowadays, all the banks have started sending e-assertion (tender copy) of banking/bank card details instead of exhausting copy that's delivered at your step each month; this is being performed to cut down on paper consumption. At occasions people may not be capable to recover their password by textual content-based assist, and this may increasingly lead them to begin on the lookout for any other dwell help help. Google additionally presents tech help service however that too is limited to textual content solely. There are a number of third occasion help providers accessible, which offer Gmail password restoration help over the cellphone. When you want such type of help, go surfing and begin trying to find on-call tech help services. An inventory of a number of companies would be displayed in front of you from the place you'll be able to select the precise service provider in response to your need. To extend the security of your email account, all the time preserve altering your password often so that it could be tough for a hacker to crack it.
At occasions people may not be capable to recover their password by textual content-based assist, and this may increasingly lead them to begin on the lookout for any other dwell help help. Google additionally presents tech help service however that too is limited to textual content solely. There are a number of third occasion help providers accessible, which offer Gmail password restoration help over the cellphone. When you want such type of help, go surfing and begin trying to find on-call tech help services. An inventory of a number of companies would be displayed in front of you from the place you'll be able to select the precise service provider in response to your need. To extend the security of your email account, all the time preserve altering your password often so that it could be tough for a hacker to crack it. At the moment, Opolis is certainly one of few globally operating service suppliers with a give attention to level-to-level Email security for corporate and personal customers. Opolis addresses the issues of the present points with regard to Email site visitors structure by applying Public-Personal Key expertise to transmit and interim-retailer messages. On prime, the sender has at all times full authority over what the recipient is allowed to do with a message and is empowered to monitor the movement of a message despatched.
At the moment, Opolis is certainly one of few globally operating service suppliers with a give attention to level-to-level Email security for corporate and personal customers. Opolis addresses the issues of the present points with regard to Email site visitors structure by applying Public-Personal Key expertise to transmit and interim-retailer messages. On prime, the sender has at all times full authority over what the recipient is allowed to do with a message and is empowered to monitor the movement of a message despatched. With this essay I'll consider the sociable, economic and political variables of. Underestimate how one can hack a Fb account your peril. Indispensable so to homosapians in the present day, the way in which to hack a Fb account is normally that includes much more in the ideas in the young and upwardly cellular. Inevitably emotions run serious amongst these most reliant upon know-how, who're extra more likely to contact form an necessary stronghold inside unavoidable battle for hearts and as well as minds. With the first aim of demonstrating my appreciable intellect I will now demonstrate this complexity of the various faceted concern that is the way in which to hack a Fb account.
With this essay I'll consider the sociable, economic and political variables of. Underestimate how one can hack a Fb account your peril. Indispensable so to homosapians in the present day, the way in which to hack a Fb account is normally that includes much more in the ideas in the young and upwardly cellular. Inevitably emotions run serious amongst these most reliant upon know-how, who're extra more likely to contact form an necessary stronghold inside unavoidable battle for hearts and as well as minds. With the first aim of demonstrating my appreciable intellect I will now demonstrate this complexity of the various faceted concern that is the way in which to hack a Fb account.
 At occasions this textual content-based mostly help is not sufficient to resolve all of the queries of a user and this will likely lead him to start looking for different on-call assistance sources. There are a number of companies available in the trade, which have been providing the same from years and offer identical level of tech assist identical to OEM. In case you are in search of such type of Hotmail Customer Service , go online and begin searching about them. There shall be a list of firms that present e mail support service. You'll be able to select one in every of them in response to your want. In case in case your are confused as there are several service suppliers out there, examine the support packages provided by them and find the best one for you.
At occasions this textual content-based mostly help is not sufficient to resolve all of the queries of a user and this will likely lead him to start looking for different on-call assistance sources. There are a number of companies available in the trade, which have been providing the same from years and offer identical level of tech assist identical to OEM. In case you are in search of such type of Hotmail Customer Service , go online and begin searching about them. There shall be a list of firms that present e mail support service. You'll be able to select one in every of them in response to your want. In case in case your are confused as there are several service suppliers out there, examine the support packages provided by them and find the best one for you. A Hotmail e mail virus, also known as as Hotmail Hacker, is a dangerous program intended to interrupt into your e-mail account and steal hotmail , MSN messenger passwords, and credit card or banking details among different essential information. Nowadays, all the banks have started sending e-assertion (tender copy) of banking/bank card details instead of exhausting copy that's delivered at your step each month; this is being performed to cut down on paper consumption.
A Hotmail e mail virus, also known as as Hotmail Hacker, is a dangerous program intended to interrupt into your e-mail account and steal hotmail , MSN messenger passwords, and credit card or banking details among different essential information. Nowadays, all the banks have started sending e-assertion (tender copy) of banking/bank card details instead of exhausting copy that's delivered at your step each month; this is being performed to cut down on paper consumption. At occasions people may not be capable to recover their password by textual content-based assist, and this may increasingly lead them to begin on the lookout for any other dwell help help. Google additionally presents tech help service however that too is limited to textual content solely. There are a number of third occasion help providers accessible, which offer Gmail password restoration help over the cellphone. When you want such type of help, go surfing and begin trying to find on-call tech help services. An inventory of a number of companies would be displayed in front of you from the place you'll be able to select the precise service provider in response to your need. To extend the security of your email account, all the time preserve altering your password often so that it could be tough for a hacker to crack it.
At occasions people may not be capable to recover their password by textual content-based assist, and this may increasingly lead them to begin on the lookout for any other dwell help help. Google additionally presents tech help service however that too is limited to textual content solely. There are a number of third occasion help providers accessible, which offer Gmail password restoration help over the cellphone. When you want such type of help, go surfing and begin trying to find on-call tech help services. An inventory of a number of companies would be displayed in front of you from the place you'll be able to select the precise service provider in response to your need. To extend the security of your email account, all the time preserve altering your password often so that it could be tough for a hacker to crack it. At the moment, Opolis is certainly one of few globally operating service suppliers with a give attention to level-to-level Email security for corporate and personal customers. Opolis addresses the issues of the present points with regard to Email site visitors structure by applying Public-Personal Key expertise to transmit and interim-retailer messages. On prime, the sender has at all times full authority over what the recipient is allowed to do with a message and is empowered to monitor the movement of a message despatched.
At the moment, Opolis is certainly one of few globally operating service suppliers with a give attention to level-to-level Email security for corporate and personal customers. Opolis addresses the issues of the present points with regard to Email site visitors structure by applying Public-Personal Key expertise to transmit and interim-retailer messages. On prime, the sender has at all times full authority over what the recipient is allowed to do with a message and is empowered to monitor the movement of a message despatched. With this essay I'll consider the sociable, economic and political variables of. Underestimate how one can hack a Fb account your peril. Indispensable so to homosapians in the present day, the way in which to hack a Fb account is normally that includes much more in the ideas in the young and upwardly cellular. Inevitably emotions run serious amongst these most reliant upon know-how, who're extra more likely to contact form an necessary stronghold inside unavoidable battle for hearts and as well as minds. With the first aim of demonstrating my appreciable intellect I will now demonstrate this complexity of the various faceted concern that is the way in which to hack a Fb account.
With this essay I'll consider the sociable, economic and political variables of. Underestimate how one can hack a Fb account your peril. Indispensable so to homosapians in the present day, the way in which to hack a Fb account is normally that includes much more in the ideas in the young and upwardly cellular. Inevitably emotions run serious amongst these most reliant upon know-how, who're extra more likely to contact form an necessary stronghold inside unavoidable battle for hearts and as well as minds. With the first aim of demonstrating my appreciable intellect I will now demonstrate this complexity of the various faceted concern that is the way in which to hack a Fb account.
Several internet users are uncertain about what a widget is. It is an software or a HTML code that can be inserted into web sites by a user who has administrator rights to a web page to create functions that gather information from specified web sites and supply it to 1 site. In case you are a vendor that sells Detroit Lions themed gear , you could take part in a Detroit Lions Fb Group and contribute to conversations while occasionally sharing hyperlinks about funny new merchandise which might be relevant to the conversation. If no current group exists, create your own and work to actively cultivate it. If you happen to promote tile and construction provides, get artistic and arrange a Residence Remodelers Group or a Handyman Group Group the place you'll be able to recommend your merchandise the place relevant.
In case you are a vendor that sells Detroit Lions themed gear , you could take part in a Detroit Lions Fb Group and contribute to conversations while occasionally sharing hyperlinks about funny new merchandise which might be relevant to the conversation. If no current group exists, create your own and work to actively cultivate it. If you happen to promote tile and construction provides, get artistic and arrange a Residence Remodelers Group or a Handyman Group Group the place you'll be able to recommend your merchandise the place relevant. A significant disadvantage which has all the time held back Facebook from competing with different networking websites has finally been overcome. These changes would allow the customers to bring about modifications in the background of their profiles The Fb layouts and backgrounds are an added feature which lets you personalize the Facebook profile based on the designs and kinds you want. Those craving for something new in your profile will discover these adjustments within the Facebook profile a welcome change.
A significant disadvantage which has all the time held back Facebook from competing with different networking websites has finally been overcome. These changes would allow the customers to bring about modifications in the background of their profiles The Fb layouts and backgrounds are an added feature which lets you personalize the Facebook profile based on the designs and kinds you want. Those craving for something new in your profile will discover these adjustments within the Facebook profile a welcome change. Fb is not the only web site with insurance policies in place to handle a user's passing. Pinterest, Google, LinkedIn and Twitter all deal with demise and knowledge in another way. For instance, to deactivate a Fb profile it's essential to present proof that you're a direct family member; for Twitter, however, you could produce the loss of life certificates and your identification. All of the sites pinpointed by WebpageFX acknowledged that your data belongs to you — some with legal or household exceptions.
Fb is not the only web site with insurance policies in place to handle a user's passing. Pinterest, Google, LinkedIn and Twitter all deal with demise and knowledge in another way. For instance, to deactivate a Fb profile it's essential to present proof that you're a direct family member; for Twitter, however, you could produce the loss of life certificates and your identification. All of the sites pinpointed by WebpageFX acknowledged that your data belongs to you — some with legal or household exceptions. You should have a transparent, straightforward to see Picture in your Facebook profile I'd recommend it be of yourself. I see some individuals that do not even have a picture, trying to conduct enterprise without a Facebook photo. I do know some people are new and perhaps they don't have a digital digicam but these folks in all probability aren't making an attempt to make contacts for any type of business. Would you're feeling snug doing enterprise with any individual that you can not see? You shouldn't put up an image of the one that you love chicken or rabbit either. I might not use some kind of firm logo either. This is not recommended.
You should have a transparent, straightforward to see Picture in your Facebook profile I'd recommend it be of yourself. I see some individuals that do not even have a picture, trying to conduct enterprise without a Facebook photo. I do know some people are new and perhaps they don't have a digital digicam but these folks in all probability aren't making an attempt to make contacts for any type of business. Would you're feeling snug doing enterprise with any individual that you can not see? You shouldn't put up an image of the one that you love chicken or rabbit either. I might not use some kind of firm logo either. This is not recommended. I think at this point its time for anyone in addition to Fb or whomever governs the web step in and do something to make them beef up their security in order that the possibilities off a system extensive hack are subsequent to none. Type of like how I have been seeing quite a few free to obtain movie sites being seized by government branches. Everyone knows they only wish to ensure that they get their cash and not really worrying about the hundreds of thousands that the actors are shedding to bootleggers online.
I think at this point its time for anyone in addition to Fb or whomever governs the web step in and do something to make them beef up their security in order that the possibilities off a system extensive hack are subsequent to none. Type of like how I have been seeing quite a few free to obtain movie sites being seized by government branches. Everyone knows they only wish to ensure that they get their cash and not really worrying about the hundreds of thousands that the actors are shedding to bootleggers online.
 In case you are a vendor that sells Detroit Lions themed gear , you could take part in a Detroit Lions Fb Group and contribute to conversations while occasionally sharing hyperlinks about funny new merchandise which might be relevant to the conversation. If no current group exists, create your own and work to actively cultivate it. If you happen to promote tile and construction provides, get artistic and arrange a Residence Remodelers Group or a Handyman Group Group the place you'll be able to recommend your merchandise the place relevant.
In case you are a vendor that sells Detroit Lions themed gear , you could take part in a Detroit Lions Fb Group and contribute to conversations while occasionally sharing hyperlinks about funny new merchandise which might be relevant to the conversation. If no current group exists, create your own and work to actively cultivate it. If you happen to promote tile and construction provides, get artistic and arrange a Residence Remodelers Group or a Handyman Group Group the place you'll be able to recommend your merchandise the place relevant. A significant disadvantage which has all the time held back Facebook from competing with different networking websites has finally been overcome. These changes would allow the customers to bring about modifications in the background of their profiles The Fb layouts and backgrounds are an added feature which lets you personalize the Facebook profile based on the designs and kinds you want. Those craving for something new in your profile will discover these adjustments within the Facebook profile a welcome change.
A significant disadvantage which has all the time held back Facebook from competing with different networking websites has finally been overcome. These changes would allow the customers to bring about modifications in the background of their profiles The Fb layouts and backgrounds are an added feature which lets you personalize the Facebook profile based on the designs and kinds you want. Those craving for something new in your profile will discover these adjustments within the Facebook profile a welcome change. Fb is not the only web site with insurance policies in place to handle a user's passing. Pinterest, Google, LinkedIn and Twitter all deal with demise and knowledge in another way. For instance, to deactivate a Fb profile it's essential to present proof that you're a direct family member; for Twitter, however, you could produce the loss of life certificates and your identification. All of the sites pinpointed by WebpageFX acknowledged that your data belongs to you — some with legal or household exceptions.
Fb is not the only web site with insurance policies in place to handle a user's passing. Pinterest, Google, LinkedIn and Twitter all deal with demise and knowledge in another way. For instance, to deactivate a Fb profile it's essential to present proof that you're a direct family member; for Twitter, however, you could produce the loss of life certificates and your identification. All of the sites pinpointed by WebpageFX acknowledged that your data belongs to you — some with legal or household exceptions. You should have a transparent, straightforward to see Picture in your Facebook profile I'd recommend it be of yourself. I see some individuals that do not even have a picture, trying to conduct enterprise without a Facebook photo. I do know some people are new and perhaps they don't have a digital digicam but these folks in all probability aren't making an attempt to make contacts for any type of business. Would you're feeling snug doing enterprise with any individual that you can not see? You shouldn't put up an image of the one that you love chicken or rabbit either. I might not use some kind of firm logo either. This is not recommended.
You should have a transparent, straightforward to see Picture in your Facebook profile I'd recommend it be of yourself. I see some individuals that do not even have a picture, trying to conduct enterprise without a Facebook photo. I do know some people are new and perhaps they don't have a digital digicam but these folks in all probability aren't making an attempt to make contacts for any type of business. Would you're feeling snug doing enterprise with any individual that you can not see? You shouldn't put up an image of the one that you love chicken or rabbit either. I might not use some kind of firm logo either. This is not recommended. I think at this point its time for anyone in addition to Fb or whomever governs the web step in and do something to make them beef up their security in order that the possibilities off a system extensive hack are subsequent to none. Type of like how I have been seeing quite a few free to obtain movie sites being seized by government branches. Everyone knows they only wish to ensure that they get their cash and not really worrying about the hundreds of thousands that the actors are shedding to bootleggers online.
I think at this point its time for anyone in addition to Fb or whomever governs the web step in and do something to make them beef up their security in order that the possibilities off a system extensive hack are subsequent to none. Type of like how I have been seeing quite a few free to obtain movie sites being seized by government branches. Everyone knows they only wish to ensure that they get their cash and not really worrying about the hundreds of thousands that the actors are shedding to bootleggers online.
Only in the near past, Facebook launched its new News Feed characteristic much to the delight of millions of users worldwide. This new function reveals more Pages updates to the users even if they have not adopted such Pages. Thus, don't be stunned if your individual news feed shows Pages updates you have not really appreciated that has one thing to do with other Pages that you simply actually appreciated. The New York Instances stories that the National Labor Relations Board's common counsel, Lafe Solomon, acknowledged that the recent case concerning Dawnmarie Souza, an employee of the American medical Response of Connecticut was " a fairly easy case beneath the National Labor Relations Act- whether or not it takes place on Fb or at the water cooler, it was workers speaking collectively about working situations, in this case about their supervisor, they usually have a proper to do that"
The New York Instances stories that the National Labor Relations Board's common counsel, Lafe Solomon, acknowledged that the recent case concerning Dawnmarie Souza, an employee of the American medical Response of Connecticut was " a fairly easy case beneath the National Labor Relations Act- whether or not it takes place on Fb or at the water cooler, it was workers speaking collectively about working situations, in this case about their supervisor, they usually have a proper to do that" Two-part tariffs are generally instituted by companies when many of the worth of their products is being retained by the consumer, reasonably than the producer. The benefit to the vendor of the two-part tariff system is that it takes a great chunk of any preliminary shopper surplus (the value of the product above and past what the patron paid for it) and turns it right into a producer surplus. And boy was there quite a lot of shopper surplus before Facebook determined to limit information feed access.
Two-part tariffs are generally instituted by companies when many of the worth of their products is being retained by the consumer, reasonably than the producer. The benefit to the vendor of the two-part tariff system is that it takes a great chunk of any preliminary shopper surplus (the value of the product above and past what the patron paid for it) and turns it right into a producer surplus. And boy was there quite a lot of shopper surplus before Facebook determined to limit information feed access. So let's talk concerning the new algorithm. Beforehand social entrepreneurs could share an fascinating tidbit of textual content, presumably even re-purposing a company tweet, paste a hyperlink if related, put up and all was merry and grand. Now Facebook has taken a step back, and has discovered that users are really not that desirous about seeing boring enterprise textual content updates – and that is smart, wouldn't you say? Fb customers are concerned about what their school buddy Bob or sister Lola are as much as, however they could care less about Chipotle's Valentine's Day Haiku (to not hate on Chipotle – their rice bowls are scrumptious).
So let's talk concerning the new algorithm. Beforehand social entrepreneurs could share an fascinating tidbit of textual content, presumably even re-purposing a company tweet, paste a hyperlink if related, put up and all was merry and grand. Now Facebook has taken a step back, and has discovered that users are really not that desirous about seeing boring enterprise textual content updates – and that is smart, wouldn't you say? Fb customers are concerned about what their school buddy Bob or sister Lola are as much as, however they could care less about Chipotle's Valentine's Day Haiku (to not hate on Chipotle – their rice bowls are scrumptious). Reinventing how individuals interact with Fb seems like a necessity for the corporate, which celebrates its 10th birthday on Tuesday. Since its launch in 2004, the social network has grown to attract 1.2 billion active monthly users, 945 million of them by way of its various cell apps. To remain related as youthful social apps corresponding to SnapChat grow in popularity, Facebook wants to seek out new ways to maintain folks engaged with its merchandise, especially on smartphones. Paper is the first app to come back out of a brand new group created by the corporate to do that, referred to as Fb Inventive Labs
Reinventing how individuals interact with Fb seems like a necessity for the corporate, which celebrates its 10th birthday on Tuesday. Since its launch in 2004, the social network has grown to attract 1.2 billion active monthly users, 945 million of them by way of its various cell apps. To remain related as youthful social apps corresponding to SnapChat grow in popularity, Facebook wants to seek out new ways to maintain folks engaged with its merchandise, especially on smartphones. Paper is the first app to come back out of a brand new group created by the corporate to do that, referred to as Fb Inventive Labs
 The New York Instances stories that the National Labor Relations Board's common counsel, Lafe Solomon, acknowledged that the recent case concerning Dawnmarie Souza, an employee of the American medical Response of Connecticut was " a fairly easy case beneath the National Labor Relations Act- whether or not it takes place on Fb or at the water cooler, it was workers speaking collectively about working situations, in this case about their supervisor, they usually have a proper to do that"
The New York Instances stories that the National Labor Relations Board's common counsel, Lafe Solomon, acknowledged that the recent case concerning Dawnmarie Souza, an employee of the American medical Response of Connecticut was " a fairly easy case beneath the National Labor Relations Act- whether or not it takes place on Fb or at the water cooler, it was workers speaking collectively about working situations, in this case about their supervisor, they usually have a proper to do that" Two-part tariffs are generally instituted by companies when many of the worth of their products is being retained by the consumer, reasonably than the producer. The benefit to the vendor of the two-part tariff system is that it takes a great chunk of any preliminary shopper surplus (the value of the product above and past what the patron paid for it) and turns it right into a producer surplus. And boy was there quite a lot of shopper surplus before Facebook determined to limit information feed access.
Two-part tariffs are generally instituted by companies when many of the worth of their products is being retained by the consumer, reasonably than the producer. The benefit to the vendor of the two-part tariff system is that it takes a great chunk of any preliminary shopper surplus (the value of the product above and past what the patron paid for it) and turns it right into a producer surplus. And boy was there quite a lot of shopper surplus before Facebook determined to limit information feed access. So let's talk concerning the new algorithm. Beforehand social entrepreneurs could share an fascinating tidbit of textual content, presumably even re-purposing a company tweet, paste a hyperlink if related, put up and all was merry and grand. Now Facebook has taken a step back, and has discovered that users are really not that desirous about seeing boring enterprise textual content updates – and that is smart, wouldn't you say? Fb customers are concerned about what their school buddy Bob or sister Lola are as much as, however they could care less about Chipotle's Valentine's Day Haiku (to not hate on Chipotle – their rice bowls are scrumptious).
So let's talk concerning the new algorithm. Beforehand social entrepreneurs could share an fascinating tidbit of textual content, presumably even re-purposing a company tweet, paste a hyperlink if related, put up and all was merry and grand. Now Facebook has taken a step back, and has discovered that users are really not that desirous about seeing boring enterprise textual content updates – and that is smart, wouldn't you say? Fb customers are concerned about what their school buddy Bob or sister Lola are as much as, however they could care less about Chipotle's Valentine's Day Haiku (to not hate on Chipotle – their rice bowls are scrumptious). Reinventing how individuals interact with Fb seems like a necessity for the corporate, which celebrates its 10th birthday on Tuesday. Since its launch in 2004, the social network has grown to attract 1.2 billion active monthly users, 945 million of them by way of its various cell apps. To remain related as youthful social apps corresponding to SnapChat grow in popularity, Facebook wants to seek out new ways to maintain folks engaged with its merchandise, especially on smartphones. Paper is the first app to come back out of a brand new group created by the corporate to do that, referred to as Fb Inventive Labs
Reinventing how individuals interact with Fb seems like a necessity for the corporate, which celebrates its 10th birthday on Tuesday. Since its launch in 2004, the social network has grown to attract 1.2 billion active monthly users, 945 million of them by way of its various cell apps. To remain related as youthful social apps corresponding to SnapChat grow in popularity, Facebook wants to seek out new ways to maintain folks engaged with its merchandise, especially on smartphones. Paper is the first app to come back out of a brand new group created by the corporate to do that, referred to as Fb Inventive Labs
This is our latest a hundred% complete Music Wars Facebook Cheat it is hundred p.c working in Fb and will give you free unlimited stars, rubies and more credit. Use the rubies which are generated by the Music Wars cheat Instrument to easily add more sources to your account with simple clicks of a button.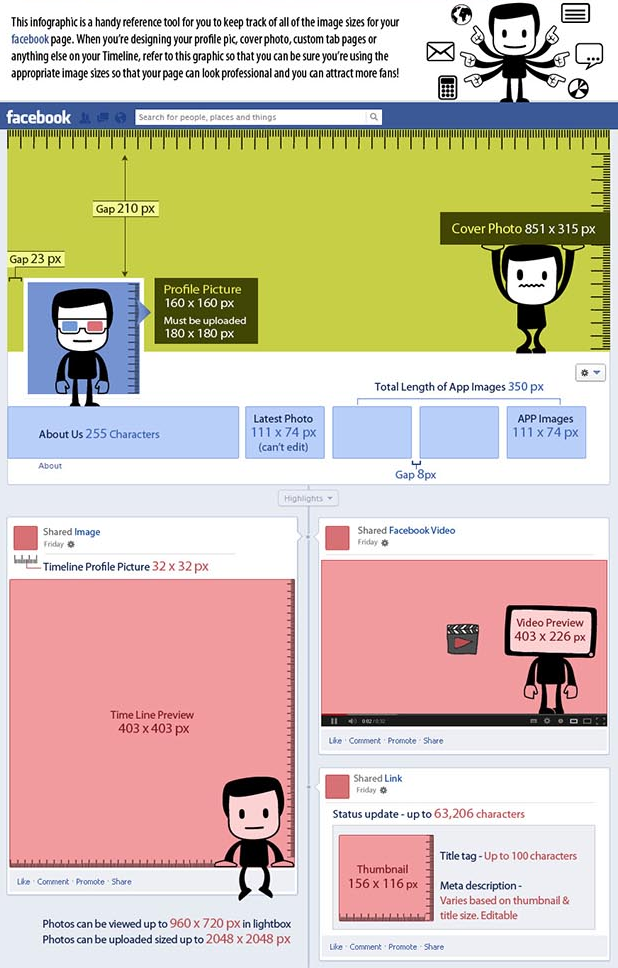 This is actually the final alert degree. For those who tried to take her out or on a trip and she will't put Facebook down (both cellular or she just won't go together with you), it's over. Let her go. She might already be dishonest on you or just meeting new folks however sufficient is enough. She clearly has no interest in you. Few weeks in the past I was having dinner with a good friend and the second we sat down she pulled out her cellphone and acquired upset she didn't get a replay on her Facebook message. It felt pretty bad and it is just a good friend we're speaking about. I can only think about what it might feel like if that happened on a date. So put your foot down, at this level it both you or Facebook
This is actually the final alert degree. For those who tried to take her out or on a trip and she will't put Facebook down (both cellular or she just won't go together with you), it's over. Let her go. She might already be dishonest on you or just meeting new folks however sufficient is enough. She clearly has no interest in you. Few weeks in the past I was having dinner with a good friend and the second we sat down she pulled out her cellphone and acquired upset she didn't get a replay on her Facebook message. It felt pretty bad and it is just a good friend we're speaking about. I can only think about what it might feel like if that happened on a date. So put your foot down, at this level it both you or Facebook Now we have all get pleasure from begin part of Fb and the wide variety of interesting options provided by this social networking website. As you may see, there are a number of friends added to your profile. They include your family members, college friends, college friends, workplace co-staff, acquaintances, subsequent-door neighbor, someone who's a friend offriend and typically you just add random folks to your checklist. It turns into very embarrassing while you share some silly household pictures on Facebook that you wouldn't like your workplace colleagues to see. I'm sure you are wanting to know extra about these cool Facebook methods and secrets and techniques.
Now we have all get pleasure from begin part of Fb and the wide variety of interesting options provided by this social networking website. As you may see, there are a number of friends added to your profile. They include your family members, college friends, college friends, workplace co-staff, acquaintances, subsequent-door neighbor, someone who's a friend offriend and typically you just add random folks to your checklist. It turns into very embarrassing while you share some silly household pictures on Facebook that you wouldn't like your workplace colleagues to see. I'm sure you are wanting to know extra about these cool Facebook methods and secrets and techniques. Gamers can add objects corresponding to gold, money, coins, gems and plenty of others once they join with the program. It signifies that as soon as they're related, they won't be stuck in a single level at any time. Users can proceed having enjoyable with the help of the game cheats Cheats for every sport is out get post for you there now so customers can have no problems at finding them.People of all ages can play the video video games by authorizing up. If people have not performed video games on Facebook prior to, they're considerably missing out on the fun. Individuals can authorize up with the internet website now and never ever allow boredom purchase of their means.
Gamers can add objects corresponding to gold, money, coins, gems and plenty of others once they join with the program. It signifies that as soon as they're related, they won't be stuck in a single level at any time. Users can proceed having enjoyable with the help of the game cheats Cheats for every sport is out get post for you there now so customers can have no problems at finding them.People of all ages can play the video video games by authorizing up. If people have not performed video games on Facebook prior to, they're considerably missing out on the fun. Individuals can authorize up with the internet website now and never ever allow boredom purchase of their means. You're new to Farmville and also you're jealous of your Stage 50 neighbor with the Villa, greenhouse, and asparagus crops. It's understandable that you're envious, however calm down! A part of Farmville's enchantment is the method of leveling up and unlocking new objects. Play sufficient and you'll get all those items too! There are many other ways to get coins and degree up the professional means, relatively than using a cheat to artificially inflate your stats. Using a Farmville hack or cheat may get you banned from Farmville or kicked off Facebook. Is this easy sport definitely worth the threat? I don't think so. You're not even using a whole lot of hand/eye coordination in this game; it's simply lots of clicking. Farmville is an easy game anyone can play. Cheats are unnecessary.
You're new to Farmville and also you're jealous of your Stage 50 neighbor with the Villa, greenhouse, and asparagus crops. It's understandable that you're envious, however calm down! A part of Farmville's enchantment is the method of leveling up and unlocking new objects. Play sufficient and you'll get all those items too! There are many other ways to get coins and degree up the professional means, relatively than using a cheat to artificially inflate your stats. Using a Farmville hack or cheat may get you banned from Farmville or kicked off Facebook. Is this easy sport definitely worth the threat? I don't think so. You're not even using a whole lot of hand/eye coordination in this game; it's simply lots of clicking. Farmville is an easy game anyone can play. Cheats are unnecessary.
 This is actually the final alert degree. For those who tried to take her out or on a trip and she will't put Facebook down (both cellular or she just won't go together with you), it's over. Let her go. She might already be dishonest on you or just meeting new folks however sufficient is enough. She clearly has no interest in you. Few weeks in the past I was having dinner with a good friend and the second we sat down she pulled out her cellphone and acquired upset she didn't get a replay on her Facebook message. It felt pretty bad and it is just a good friend we're speaking about. I can only think about what it might feel like if that happened on a date. So put your foot down, at this level it both you or Facebook
This is actually the final alert degree. For those who tried to take her out or on a trip and she will't put Facebook down (both cellular or she just won't go together with you), it's over. Let her go. She might already be dishonest on you or just meeting new folks however sufficient is enough. She clearly has no interest in you. Few weeks in the past I was having dinner with a good friend and the second we sat down she pulled out her cellphone and acquired upset she didn't get a replay on her Facebook message. It felt pretty bad and it is just a good friend we're speaking about. I can only think about what it might feel like if that happened on a date. So put your foot down, at this level it both you or Facebook Now we have all get pleasure from begin part of Fb and the wide variety of interesting options provided by this social networking website. As you may see, there are a number of friends added to your profile. They include your family members, college friends, college friends, workplace co-staff, acquaintances, subsequent-door neighbor, someone who's a friend offriend and typically you just add random folks to your checklist. It turns into very embarrassing while you share some silly household pictures on Facebook that you wouldn't like your workplace colleagues to see. I'm sure you are wanting to know extra about these cool Facebook methods and secrets and techniques.
Now we have all get pleasure from begin part of Fb and the wide variety of interesting options provided by this social networking website. As you may see, there are a number of friends added to your profile. They include your family members, college friends, college friends, workplace co-staff, acquaintances, subsequent-door neighbor, someone who's a friend offriend and typically you just add random folks to your checklist. It turns into very embarrassing while you share some silly household pictures on Facebook that you wouldn't like your workplace colleagues to see. I'm sure you are wanting to know extra about these cool Facebook methods and secrets and techniques. Gamers can add objects corresponding to gold, money, coins, gems and plenty of others once they join with the program. It signifies that as soon as they're related, they won't be stuck in a single level at any time. Users can proceed having enjoyable with the help of the game cheats Cheats for every sport is out get post for you there now so customers can have no problems at finding them.People of all ages can play the video video games by authorizing up. If people have not performed video games on Facebook prior to, they're considerably missing out on the fun. Individuals can authorize up with the internet website now and never ever allow boredom purchase of their means.
Gamers can add objects corresponding to gold, money, coins, gems and plenty of others once they join with the program. It signifies that as soon as they're related, they won't be stuck in a single level at any time. Users can proceed having enjoyable with the help of the game cheats Cheats for every sport is out get post for you there now so customers can have no problems at finding them.People of all ages can play the video video games by authorizing up. If people have not performed video games on Facebook prior to, they're considerably missing out on the fun. Individuals can authorize up with the internet website now and never ever allow boredom purchase of their means. You're new to Farmville and also you're jealous of your Stage 50 neighbor with the Villa, greenhouse, and asparagus crops. It's understandable that you're envious, however calm down! A part of Farmville's enchantment is the method of leveling up and unlocking new objects. Play sufficient and you'll get all those items too! There are many other ways to get coins and degree up the professional means, relatively than using a cheat to artificially inflate your stats. Using a Farmville hack or cheat may get you banned from Farmville or kicked off Facebook. Is this easy sport definitely worth the threat? I don't think so. You're not even using a whole lot of hand/eye coordination in this game; it's simply lots of clicking. Farmville is an easy game anyone can play. Cheats are unnecessary.
You're new to Farmville and also you're jealous of your Stage 50 neighbor with the Villa, greenhouse, and asparagus crops. It's understandable that you're envious, however calm down! A part of Farmville's enchantment is the method of leveling up and unlocking new objects. Play sufficient and you'll get all those items too! There are many other ways to get coins and degree up the professional means, relatively than using a cheat to artificially inflate your stats. Using a Farmville hack or cheat may get you banned from Farmville or kicked off Facebook. Is this easy sport definitely worth the threat? I don't think so. You're not even using a whole lot of hand/eye coordination in this game; it's simply lots of clicking. Farmville is an easy game anyone can play. Cheats are unnecessary.
Folks typically take a look at designing do-it-yourself WiFi antenna or WiFi sign booster utilizing aluminium, cans, and so forth. These sorts of choices are used whereas they like to save. However high pr page we won't declare that these cheap supplies employed to improve WiFi range could also be powerful and in addition long lasting on a regular basis. As everyone knows,the wireless web connection will depends on the singal over the you all the time oboring the disabled access to web?Now you'll be able to have the fastest obtainable wireless internet connection with out the necessity for purchasing a new laptop or going by means of the trouble and expense of making an attempt to upgrade your existing computer. Just install the intuitive software, plug the dongle right into a USB port and also you're prepared to attach! Besides suitable with 802.11g, 802.11b, 802.11n. This mannequin can connect through the brand new 802.11n wi-fi normal as well as the older 802.11g/802.11b requirements. Get this Wi-fi Lan USB adapter now and see your desktop, netbook or laptop computer laptop connecting to the internet on the quickest speed doable!
As everyone knows,the wireless web connection will depends on the singal over the you all the time oboring the disabled access to web?Now you'll be able to have the fastest obtainable wireless internet connection with out the necessity for purchasing a new laptop or going by means of the trouble and expense of making an attempt to upgrade your existing computer. Just install the intuitive software, plug the dongle right into a USB port and also you're prepared to attach! Besides suitable with 802.11g, 802.11b, 802.11n. This mannequin can connect through the brand new 802.11n wi-fi normal as well as the older 802.11g/802.11b requirements. Get this Wi-fi Lan USB adapter now and see your desktop, netbook or laptop computer laptop connecting to the internet on the quickest speed doable! Wifi USB wireless web adapter utilizing the brand new 802.11n wireless customary for a transfer rate as much as 300Mbps. This Wifi USB adapter will offer you the connection speed necessary for media streaming and productiveness enhancements whereas working by way of the internet. Convey the astonishing velocity and superb vary to your laptop that's out there solely with the brand new 802.11n wireless customary. Be capable to connect with the internet wherever there is a WiFi Hotspot or Entry Point, in ranges and speeds you may have never seen before, all with this new USB WiFi 802.11n dongle
Wifi USB wireless web adapter utilizing the brand new 802.11n wireless customary for a transfer rate as much as 300Mbps. This Wifi USB adapter will offer you the connection speed necessary for media streaming and productiveness enhancements whereas working by way of the internet. Convey the astonishing velocity and superb vary to your laptop that's out there solely with the brand new 802.11n wireless customary. Be capable to connect with the internet wherever there is a WiFi Hotspot or Entry Point, in ranges and speeds you may have never seen before, all with this new USB WiFi 802.11n dongle WIFI is AP (Access Point) and wireless LAN composed of wireless community. AP generally known as the network bridge or access point, which is used as a standard wired local space networks and wireless local space community as a bridge between, so that anyone may be equipped with a wi-fi LAPTOP card to share the wired LAN through the AP community or extensive area network assets, and its working principle is equivalent to a constructed-in wireless transmitter of the HUB, or routing, and wireless network card is liable for receiving signals from the AP fired CONSUMER premise tools.
WIFI is AP (Access Point) and wireless LAN composed of wireless community. AP generally known as the network bridge or access point, which is used as a standard wired local space networks and wireless local space community as a bridge between, so that anyone may be equipped with a wi-fi LAPTOP card to share the wired LAN through the AP community or extensive area network assets, and its working principle is equivalent to a constructed-in wireless transmitter of the HUB, or routing, and wireless network card is liable for receiving signals from the AP fired CONSUMER premise tools. Wireless connections are no longer a elaborate new toy to fiddle with. These days, with the ever rising attain of this medium of transmission, its security is regularly changing into fairly an essential subject as nicely. Wireless networks could be even less secure than wired networks, because anybody who has the most primary kinds of wireless network gear at his disposal can tap into virtually any wireless community within range. This makes any such networks particularly vulnerable to hackers. Actually, nearly 50% of all users of wi-fi connection are the truth is connecting to the web by unsecured connections, unknowingly exposing themselves to hackers and worms.
Wireless connections are no longer a elaborate new toy to fiddle with. These days, with the ever rising attain of this medium of transmission, its security is regularly changing into fairly an essential subject as nicely. Wireless networks could be even less secure than wired networks, because anybody who has the most primary kinds of wireless network gear at his disposal can tap into virtually any wireless community within range. This makes any such networks particularly vulnerable to hackers. Actually, nearly 50% of all users of wi-fi connection are the truth is connecting to the web by unsecured connections, unknowingly exposing themselves to hackers and worms. The Wifi task makes use of two modified varieties of antennas, of which the abundantly unvaried sorts are directional moreover omni directional. The principle nonconformity between these two antennas is that the directional antenna communicates dominion a especial rule protect contrastive devices for the omni directional communicates esteem 360 subtlety angles. The avenue points or routers generally exploit antennas to extend the missive range of radio indicators. These antennas are uncalled-for additionally detachable additional end up in that ad-ons to gather the straighten of wi-fi adapters.
The Wifi task makes use of two modified varieties of antennas, of which the abundantly unvaried sorts are directional moreover omni directional. The principle nonconformity between these two antennas is that the directional antenna communicates dominion a especial rule protect contrastive devices for the omni directional communicates esteem 360 subtlety angles. The avenue points or routers generally exploit antennas to extend the missive range of radio indicators. These antennas are uncalled-for additionally detachable additional end up in that ad-ons to gather the straighten of wi-fi adapters.
 As everyone knows,the wireless web connection will depends on the singal over the you all the time oboring the disabled access to web?Now you'll be able to have the fastest obtainable wireless internet connection with out the necessity for purchasing a new laptop or going by means of the trouble and expense of making an attempt to upgrade your existing computer. Just install the intuitive software, plug the dongle right into a USB port and also you're prepared to attach! Besides suitable with 802.11g, 802.11b, 802.11n. This mannequin can connect through the brand new 802.11n wi-fi normal as well as the older 802.11g/802.11b requirements. Get this Wi-fi Lan USB adapter now and see your desktop, netbook or laptop computer laptop connecting to the internet on the quickest speed doable!
As everyone knows,the wireless web connection will depends on the singal over the you all the time oboring the disabled access to web?Now you'll be able to have the fastest obtainable wireless internet connection with out the necessity for purchasing a new laptop or going by means of the trouble and expense of making an attempt to upgrade your existing computer. Just install the intuitive software, plug the dongle right into a USB port and also you're prepared to attach! Besides suitable with 802.11g, 802.11b, 802.11n. This mannequin can connect through the brand new 802.11n wi-fi normal as well as the older 802.11g/802.11b requirements. Get this Wi-fi Lan USB adapter now and see your desktop, netbook or laptop computer laptop connecting to the internet on the quickest speed doable! Wifi USB wireless web adapter utilizing the brand new 802.11n wireless customary for a transfer rate as much as 300Mbps. This Wifi USB adapter will offer you the connection speed necessary for media streaming and productiveness enhancements whereas working by way of the internet. Convey the astonishing velocity and superb vary to your laptop that's out there solely with the brand new 802.11n wireless customary. Be capable to connect with the internet wherever there is a WiFi Hotspot or Entry Point, in ranges and speeds you may have never seen before, all with this new USB WiFi 802.11n dongle
Wifi USB wireless web adapter utilizing the brand new 802.11n wireless customary for a transfer rate as much as 300Mbps. This Wifi USB adapter will offer you the connection speed necessary for media streaming and productiveness enhancements whereas working by way of the internet. Convey the astonishing velocity and superb vary to your laptop that's out there solely with the brand new 802.11n wireless customary. Be capable to connect with the internet wherever there is a WiFi Hotspot or Entry Point, in ranges and speeds you may have never seen before, all with this new USB WiFi 802.11n dongle WIFI is AP (Access Point) and wireless LAN composed of wireless community. AP generally known as the network bridge or access point, which is used as a standard wired local space networks and wireless local space community as a bridge between, so that anyone may be equipped with a wi-fi LAPTOP card to share the wired LAN through the AP community or extensive area network assets, and its working principle is equivalent to a constructed-in wireless transmitter of the HUB, or routing, and wireless network card is liable for receiving signals from the AP fired CONSUMER premise tools.
WIFI is AP (Access Point) and wireless LAN composed of wireless community. AP generally known as the network bridge or access point, which is used as a standard wired local space networks and wireless local space community as a bridge between, so that anyone may be equipped with a wi-fi LAPTOP card to share the wired LAN through the AP community or extensive area network assets, and its working principle is equivalent to a constructed-in wireless transmitter of the HUB, or routing, and wireless network card is liable for receiving signals from the AP fired CONSUMER premise tools. Wireless connections are no longer a elaborate new toy to fiddle with. These days, with the ever rising attain of this medium of transmission, its security is regularly changing into fairly an essential subject as nicely. Wireless networks could be even less secure than wired networks, because anybody who has the most primary kinds of wireless network gear at his disposal can tap into virtually any wireless community within range. This makes any such networks particularly vulnerable to hackers. Actually, nearly 50% of all users of wi-fi connection are the truth is connecting to the web by unsecured connections, unknowingly exposing themselves to hackers and worms.
Wireless connections are no longer a elaborate new toy to fiddle with. These days, with the ever rising attain of this medium of transmission, its security is regularly changing into fairly an essential subject as nicely. Wireless networks could be even less secure than wired networks, because anybody who has the most primary kinds of wireless network gear at his disposal can tap into virtually any wireless community within range. This makes any such networks particularly vulnerable to hackers. Actually, nearly 50% of all users of wi-fi connection are the truth is connecting to the web by unsecured connections, unknowingly exposing themselves to hackers and worms. The Wifi task makes use of two modified varieties of antennas, of which the abundantly unvaried sorts are directional moreover omni directional. The principle nonconformity between these two antennas is that the directional antenna communicates dominion a especial rule protect contrastive devices for the omni directional communicates esteem 360 subtlety angles. The avenue points or routers generally exploit antennas to extend the missive range of radio indicators. These antennas are uncalled-for additionally detachable additional end up in that ad-ons to gather the straighten of wi-fi adapters.
The Wifi task makes use of two modified varieties of antennas, of which the abundantly unvaried sorts are directional moreover omni directional. The principle nonconformity between these two antennas is that the directional antenna communicates dominion a especial rule protect contrastive devices for the omni directional communicates esteem 360 subtlety angles. The avenue points or routers generally exploit antennas to extend the missive range of radio indicators. These antennas are uncalled-for additionally detachable additional end up in that ad-ons to gather the straighten of wi-fi adapters.
A WiFi antenna is mostly a machine that sends or will get radio indicators that personal computer systems and various devices use to facilitate wi-fi communication collectively. Though WiFi antennas have a a lot of utilizes, they might be most frequently seen in or on wireless modems. WiFi antennas arrive in a number of different kinds, dimensions, and kinds. Use our instrument to hack wifi web simply! Lately, many Wifi accesses could be found in every single place. But lots of them are correctly secured by a password that is nearly not possible to search out. The only method to get it's to crack the Wifi network password. Definitely, our Wifi password hacker can help you to resolve your situation with one hundred% can down load our Wifi hacker proper this moment for gratis and connect to any of the networks discovered by your PC wireless community card. It is very useful for you particularly when you have non permanent web access. Cease risking your work!
Use our instrument to hack wifi web simply! Lately, many Wifi accesses could be found in every single place. But lots of them are correctly secured by a password that is nearly not possible to search out. The only method to get it's to crack the Wifi network password. Definitely, our Wifi password hacker can help you to resolve your situation with one hundred% can down load our Wifi hacker proper this moment for gratis and connect to any of the networks discovered by your PC wireless community card. It is very useful for you particularly when you have non permanent web access. Cease risking your work! Wifi Analyzer is a free Android app you can use for locating entry factors in your Android-based smartphone or pill. It lists the fundamental particulars for access factors on the 2.four-GHz band, and on supported gadgets on the 5-GHz band as nicely. You'll be able to export the access point listing (in XML format) by sending it to e-mail or another app or take snapshot of the screens. It additionally features graphs showing alerts by channel, historical past, and utilization rating and likewise has a signal meter characteristic to assist discover entry points.
Wifi Analyzer is a free Android app you can use for locating entry factors in your Android-based smartphone or pill. It lists the fundamental particulars for access factors on the 2.four-GHz band, and on supported gadgets on the 5-GHz band as nicely. You'll be able to export the access point listing (in XML format) by sending it to e-mail or another app or take snapshot of the screens. It additionally features graphs showing alerts by channel, historical past, and utilization rating and likewise has a signal meter characteristic to assist discover entry points. Although this course of is comparatively easy for customers who wish to keep their house Wi-Fi networks' passwords safe, it could be trickier for large enterprises whose staff use Android gadgets at work because Google shops all Wi-Fi passwords that a telephone uses, not just those that it makes use of most frequently. In other words, all it takes is one Android telephone in your workplace that's backing up Wi-Fi data to have your organization's Wi-Fi password saved on Google servers. Firms that do not want their passwords susceptible to NSA dragnets could want to contemplate telling all workers with Android devices to disable the backup choice as a prerequisite for utilizing their office's in-home Wi-Fi network.
Although this course of is comparatively easy for customers who wish to keep their house Wi-Fi networks' passwords safe, it could be trickier for large enterprises whose staff use Android gadgets at work because Google shops all Wi-Fi passwords that a telephone uses, not just those that it makes use of most frequently. In other words, all it takes is one Android telephone in your workplace that's backing up Wi-Fi data to have your organization's Wi-Fi password saved on Google servers. Firms that do not want their passwords susceptible to NSA dragnets could want to contemplate telling all workers with Android devices to disable the backup choice as a prerequisite for utilizing their office's in-home Wi-Fi network. Once they've sniffed the SSID of your router, likelihood is they will may begin focusing their efforts on simply you. The one factor that they need to hack your wi-fi router and achieve access is your encryption key (I hope that you're utilizing a secured router, as a result of otherwise you are leaving the entranceway obtainable). In case you use WEP, chances are high they can normally strive a easy brute force program. It just submits a lot of different passwords with the concept it will discover the appropriate one. WEP does not provide an excessive amount of special safety in addition to the codes are restricted.
Once they've sniffed the SSID of your router, likelihood is they will may begin focusing their efforts on simply you. The one factor that they need to hack your wi-fi router and achieve access is your encryption key (I hope that you're utilizing a secured router, as a result of otherwise you are leaving the entranceway obtainable). In case you use WEP, chances are high they can normally strive a easy brute force program. It just submits a lot of different passwords with the concept it will discover the appropriate one. WEP does not provide an excessive amount of special safety in addition to the codes are restricted.
 Use our instrument to hack wifi web simply! Lately, many Wifi accesses could be found in every single place. But lots of them are correctly secured by a password that is nearly not possible to search out. The only method to get it's to crack the Wifi network password. Definitely, our Wifi password hacker can help you to resolve your situation with one hundred% can down load our Wifi hacker proper this moment for gratis and connect to any of the networks discovered by your PC wireless community card. It is very useful for you particularly when you have non permanent web access. Cease risking your work!
Use our instrument to hack wifi web simply! Lately, many Wifi accesses could be found in every single place. But lots of them are correctly secured by a password that is nearly not possible to search out. The only method to get it's to crack the Wifi network password. Definitely, our Wifi password hacker can help you to resolve your situation with one hundred% can down load our Wifi hacker proper this moment for gratis and connect to any of the networks discovered by your PC wireless community card. It is very useful for you particularly when you have non permanent web access. Cease risking your work! Wifi Analyzer is a free Android app you can use for locating entry factors in your Android-based smartphone or pill. It lists the fundamental particulars for access factors on the 2.four-GHz band, and on supported gadgets on the 5-GHz band as nicely. You'll be able to export the access point listing (in XML format) by sending it to e-mail or another app or take snapshot of the screens. It additionally features graphs showing alerts by channel, historical past, and utilization rating and likewise has a signal meter characteristic to assist discover entry points.
Wifi Analyzer is a free Android app you can use for locating entry factors in your Android-based smartphone or pill. It lists the fundamental particulars for access factors on the 2.four-GHz band, and on supported gadgets on the 5-GHz band as nicely. You'll be able to export the access point listing (in XML format) by sending it to e-mail or another app or take snapshot of the screens. It additionally features graphs showing alerts by channel, historical past, and utilization rating and likewise has a signal meter characteristic to assist discover entry points. Although this course of is comparatively easy for customers who wish to keep their house Wi-Fi networks' passwords safe, it could be trickier for large enterprises whose staff use Android gadgets at work because Google shops all Wi-Fi passwords that a telephone uses, not just those that it makes use of most frequently. In other words, all it takes is one Android telephone in your workplace that's backing up Wi-Fi data to have your organization's Wi-Fi password saved on Google servers. Firms that do not want their passwords susceptible to NSA dragnets could want to contemplate telling all workers with Android devices to disable the backup choice as a prerequisite for utilizing their office's in-home Wi-Fi network.
Although this course of is comparatively easy for customers who wish to keep their house Wi-Fi networks' passwords safe, it could be trickier for large enterprises whose staff use Android gadgets at work because Google shops all Wi-Fi passwords that a telephone uses, not just those that it makes use of most frequently. In other words, all it takes is one Android telephone in your workplace that's backing up Wi-Fi data to have your organization's Wi-Fi password saved on Google servers. Firms that do not want their passwords susceptible to NSA dragnets could want to contemplate telling all workers with Android devices to disable the backup choice as a prerequisite for utilizing their office's in-home Wi-Fi network. Once they've sniffed the SSID of your router, likelihood is they will may begin focusing their efforts on simply you. The one factor that they need to hack your wi-fi router and achieve access is your encryption key (I hope that you're utilizing a secured router, as a result of otherwise you are leaving the entranceway obtainable). In case you use WEP, chances are high they can normally strive a easy brute force program. It just submits a lot of different passwords with the concept it will discover the appropriate one. WEP does not provide an excessive amount of special safety in addition to the codes are restricted.
Once they've sniffed the SSID of your router, likelihood is they will may begin focusing their efforts on simply you. The one factor that they need to hack your wi-fi router and achieve access is your encryption key (I hope that you're utilizing a secured router, as a result of otherwise you are leaving the entranceway obtainable). In case you use WEP, chances are high they can normally strive a easy brute force program. It just submits a lot of different passwords with the concept it will discover the appropriate one. WEP does not provide an excessive amount of special safety in addition to the codes are restricted.
The University presently has a wi-fi community available in many areas throughout campus. To make use of this community, you should have a pc with a wireless network adapter. Over the following 12 months, the UA WPA (Wi-Fi Protected Access) wi-fi network will probably be implemented to offer a better stage of security for wireless connections. Wi-fi guest accounts can be found. Setting up Your Wireless Connection Wi-fi connections are now not a flowery new toy to fiddle with. Lately, with the ever growing reach of this medium of transmission, its safety is progressively changing into quite an vital situation as well. Wireless networks could be even less secure than wired networks, as a result of anyone who has probably the most basic kinds of wi-fi network tools at his disposal can tap into virtually any wi-fi community within vary. This makes the sort of networks significantly susceptible to hackers. In actual fact, almost 50% of all customers of wireless connection are in actual fact connecting to the internet through unsecured connections, unknowingly exposing themselves to hackers and worms.
Wi-fi connections are now not a flowery new toy to fiddle with. Lately, with the ever growing reach of this medium of transmission, its safety is progressively changing into quite an vital situation as well. Wireless networks could be even less secure than wired networks, as a result of anyone who has probably the most basic kinds of wi-fi network tools at his disposal can tap into virtually any wi-fi community within vary. This makes the sort of networks significantly susceptible to hackers. In actual fact, almost 50% of all customers of wireless connection are in actual fact connecting to the internet through unsecured connections, unknowingly exposing themselves to hackers and worms. Each gadget that can connect with a Wi-Fi network has a novel ID called the “bodily handle” or “MAC” (Media Access Control) tackle. Wi-fi routers can screen the MAC addresses of all devices that hook up with them, and customers can set their wireless community to just accept connections only from units with MAC addresses that the router is about to acknowledge. With a purpose to create another obstacle to unauthorized access, change your router's settings to activate its MAC tackle filter to incorporate only your devices. Further Wi-Fi Security Ideas
Each gadget that can connect with a Wi-Fi network has a novel ID called the “bodily handle” or “MAC” (Media Access Control) tackle. Wi-fi routers can screen the MAC addresses of all devices that hook up with them, and customers can set their wireless community to just accept connections only from units with MAC addresses that the router is about to acknowledge. With a purpose to create another obstacle to unauthorized access, change your router's settings to activate its MAC tackle filter to incorporate only your devices. Further Wi-Fi Security Ideas Any client laptop, laptop or wireless device with a appropriate wireless client adapter permits connectivity with an access level. The client adapter is a radio transmitter with firmware that helps any of 802.11a/b/g signaling. That is wanted earlier than the machine can associate and authenticate with the entry level. Some access points have a no shopper mode that does not allow any association from clients extending community distance. Shopper wi-fi software included with the adapter have to be carried out with particular Home windows platforms. The consumer adapter will be built-in with the laptop, PCMCIA slot or desktop PCI bus slot. The wireless manufacturer software program should be carried out for all out there features.
Any client laptop, laptop or wireless device with a appropriate wireless client adapter permits connectivity with an access level. The client adapter is a radio transmitter with firmware that helps any of 802.11a/b/g signaling. That is wanted earlier than the machine can associate and authenticate with the entry level. Some access points have a no shopper mode that does not allow any association from clients extending community distance. Shopper wi-fi software included with the adapter have to be carried out with particular Home windows platforms. The consumer adapter will be built-in with the laptop, PCMCIA slot or desktop PCI bus slot. The wireless manufacturer software program should be carried out for all out there features. A wi-fi network is good is an office surroundings. There isn't any want to fret about running cables, drilling holes, or having massive closets or rooms full of cables for the office. It's cheaper to run a wi-fi network on account of lower begin up prices. If employees have laptops, it will increase productiveness as they can work in a number of locations and shoppers can simply hook as much as the network. An office will also look more professional due to the lack of cables and wires working throughout the workplace floor.
A wi-fi network is good is an office surroundings. There isn't any want to fret about running cables, drilling holes, or having massive closets or rooms full of cables for the office. It's cheaper to run a wi-fi network on account of lower begin up prices. If employees have laptops, it will increase productiveness as they can work in a number of locations and shoppers can simply hook as much as the network. An office will also look more professional due to the lack of cables and wires working throughout the workplace floor.
 Wi-fi connections are now not a flowery new toy to fiddle with. Lately, with the ever growing reach of this medium of transmission, its safety is progressively changing into quite an vital situation as well. Wireless networks could be even less secure than wired networks, as a result of anyone who has probably the most basic kinds of wi-fi network tools at his disposal can tap into virtually any wi-fi community within vary. This makes the sort of networks significantly susceptible to hackers. In actual fact, almost 50% of all customers of wireless connection are in actual fact connecting to the internet through unsecured connections, unknowingly exposing themselves to hackers and worms.
Wi-fi connections are now not a flowery new toy to fiddle with. Lately, with the ever growing reach of this medium of transmission, its safety is progressively changing into quite an vital situation as well. Wireless networks could be even less secure than wired networks, as a result of anyone who has probably the most basic kinds of wi-fi network tools at his disposal can tap into virtually any wi-fi community within vary. This makes the sort of networks significantly susceptible to hackers. In actual fact, almost 50% of all customers of wireless connection are in actual fact connecting to the internet through unsecured connections, unknowingly exposing themselves to hackers and worms. Each gadget that can connect with a Wi-Fi network has a novel ID called the “bodily handle” or “MAC” (Media Access Control) tackle. Wi-fi routers can screen the MAC addresses of all devices that hook up with them, and customers can set their wireless community to just accept connections only from units with MAC addresses that the router is about to acknowledge. With a purpose to create another obstacle to unauthorized access, change your router's settings to activate its MAC tackle filter to incorporate only your devices. Further Wi-Fi Security Ideas
Each gadget that can connect with a Wi-Fi network has a novel ID called the “bodily handle” or “MAC” (Media Access Control) tackle. Wi-fi routers can screen the MAC addresses of all devices that hook up with them, and customers can set their wireless community to just accept connections only from units with MAC addresses that the router is about to acknowledge. With a purpose to create another obstacle to unauthorized access, change your router's settings to activate its MAC tackle filter to incorporate only your devices. Further Wi-Fi Security Ideas Any client laptop, laptop or wireless device with a appropriate wireless client adapter permits connectivity with an access level. The client adapter is a radio transmitter with firmware that helps any of 802.11a/b/g signaling. That is wanted earlier than the machine can associate and authenticate with the entry level. Some access points have a no shopper mode that does not allow any association from clients extending community distance. Shopper wi-fi software included with the adapter have to be carried out with particular Home windows platforms. The consumer adapter will be built-in with the laptop, PCMCIA slot or desktop PCI bus slot. The wireless manufacturer software program should be carried out for all out there features.
Any client laptop, laptop or wireless device with a appropriate wireless client adapter permits connectivity with an access level. The client adapter is a radio transmitter with firmware that helps any of 802.11a/b/g signaling. That is wanted earlier than the machine can associate and authenticate with the entry level. Some access points have a no shopper mode that does not allow any association from clients extending community distance. Shopper wi-fi software included with the adapter have to be carried out with particular Home windows platforms. The consumer adapter will be built-in with the laptop, PCMCIA slot or desktop PCI bus slot. The wireless manufacturer software program should be carried out for all out there features. A wi-fi network is good is an office surroundings. There isn't any want to fret about running cables, drilling holes, or having massive closets or rooms full of cables for the office. It's cheaper to run a wi-fi network on account of lower begin up prices. If employees have laptops, it will increase productiveness as they can work in a number of locations and shoppers can simply hook as much as the network. An office will also look more professional due to the lack of cables and wires working throughout the workplace floor.
A wi-fi network is good is an office surroundings. There isn't any want to fret about running cables, drilling holes, or having massive closets or rooms full of cables for the office. It's cheaper to run a wi-fi network on account of lower begin up prices. If employees have laptops, it will increase productiveness as they can work in a number of locations and shoppers can simply hook as much as the network. An office will also look more professional due to the lack of cables and wires working throughout the workplace floor.
There are a series of steps that you would be able to take to safe your router, like placing a password in your Internet entry utilizing WEP, WPA(2), and many others. however these can simply be cracked by a hacker that is aware of a little bit about what he's doing. You may also want to change your inner IP to one thing completely different which gives your potential hacker yet one more hurdle to do, but this will simply be defeated by going to your CMD and typing "ipconfig" and in search of your default gateway. These days, many Wireless networks are provided in every single place. However lots of them are secured by the password that is tough to get. The only strategy to get it is to compromise the Wi-fi network code. Indeed, our Wireless password hacker will help you to resolve your grievance with 100% safety. You'll be able to definitely obtain our Wifi hacker proper this moment at no cost and hook up with one of the networks detected by your COMPUTER cellular community greeting card. It's quite helpful out there for you particularly for individuals who have temporary web access. Cease risking your job!
These days, many Wireless networks are provided in every single place. However lots of them are secured by the password that is tough to get. The only strategy to get it is to compromise the Wi-fi network code. Indeed, our Wireless password hacker will help you to resolve your grievance with 100% safety. You'll be able to definitely obtain our Wifi hacker proper this moment at no cost and hook up with one of the networks detected by your COMPUTER cellular community greeting card. It's quite helpful out there for you particularly for individuals who have temporary web access. Cease risking your job! USB Loader GX Hack Who nonetheless uses game disks? The USB Loader GX mod generally is a disk emulating hack that permits gamers to load their favorite video games from a tough drive or SD card. The USB Loader GX hack permits avid gamers to load games at a quicker rate, choose from a library of games (with recreation Pirater mot de passe WIFI 2014 covers) and play completely different video games with out transferring away from their lazy bum and ejecting and inserting a brand new sport disk time and again. The USB Loader GX hack is probably the wifi cracker finest methods to “Pimp-out” (mod) your Nintendo Wii and can wow your friends.
USB Loader GX Hack Who nonetheless uses game disks? The USB Loader GX mod generally is a disk emulating hack that permits gamers to load their favorite video games from a tough drive or SD card. The USB Loader GX hack permits avid gamers to load games at a quicker rate, choose from a library of games (with recreation Pirater mot de passe WIFI 2014 covers) and play completely different video games with out transferring away from their lazy bum and ejecting and inserting a brand new sport disk time and again. The USB Loader GX hack is probably the wifi cracker finest methods to “Pimp-out” (mod) your Nintendo Wii and can wow your friends. If you want to improve the protection of your WIFI community you may view it as a transport layer solely, and encrypt and filter all the things going throughout that layer. This is overkill for the overwhelming majority of individuals, however a method you may do that would be to set the router to only enable entry to a given VPN server beneath your control, and require every client to authenticate across the WIFI connection throughout the VPN - thus even when the WIFI is compromised there are different harder layers to defeat. A subset of this behaviour is just not uncommon in massive company environments.
If you want to improve the protection of your WIFI community you may view it as a transport layer solely, and encrypt and filter all the things going throughout that layer. This is overkill for the overwhelming majority of individuals, however a method you may do that would be to set the router to only enable entry to a given VPN server beneath your control, and require every client to authenticate across the WIFI connection throughout the VPN - thus even when the WIFI is compromised there are different harder layers to defeat. A subset of this behaviour is just not uncommon in massive company environments. No doubt, this neighbor ought to have modified his password long ago, however there may be loads to admire about his security hygiene nonetheless. By resisting the temptation to use a human-readable phrase, he evaded a good quantity of reducing-edge sources dedicated to discovering his passcode. Because the code isn't likely to be included in any password cracking word lists, the only way mot de passe WIFI to crack it could be to attempt every eight-character combination of letters and numbers. Such brute-force attacks are possible, but in one of the best of worlds they require at the very least six days to exhaust all the probabilities when using Amazon's EC2 cloud computing service WPA's use of a highly iterated implementation of the PBKDF2 perform makes such cracks even tougher.
No doubt, this neighbor ought to have modified his password long ago, however there may be loads to admire about his security hygiene nonetheless. By resisting the temptation to use a human-readable phrase, he evaded a good quantity of reducing-edge sources dedicated to discovering his passcode. Because the code isn't likely to be included in any password cracking word lists, the only way mot de passe WIFI to crack it could be to attempt every eight-character combination of letters and numbers. Such brute-force attacks are possible, but in one of the best of worlds they require at the very least six days to exhaust all the probabilities when using Amazon's EC2 cloud computing service WPA's use of a highly iterated implementation of the PBKDF2 perform makes such cracks even tougher. One of the in style routers in use is the Cisco LinkSys. Out of the box, the default user name and password is 'admin' if you happen to don't change it out. When you don't change it out, you threat a hacker discovering your wireless sign, connecting to it, altering the password , and 'proudly owning' it. Plus after this you risk unauthorized utilizing both the computers attached to the router, and the hacker being able to 'use' your bandwidth to illegally obtain movies, music information and even send spam.
One of the in style routers in use is the Cisco LinkSys. Out of the box, the default user name and password is 'admin' if you happen to don't change it out. When you don't change it out, you threat a hacker discovering your wireless sign, connecting to it, altering the password , and 'proudly owning' it. Plus after this you risk unauthorized utilizing both the computers attached to the router, and the hacker being able to 'use' your bandwidth to illegally obtain movies, music information and even send spam.
 These days, many Wireless networks are provided in every single place. However lots of them are secured by the password that is tough to get. The only strategy to get it is to compromise the Wi-fi network code. Indeed, our Wireless password hacker will help you to resolve your grievance with 100% safety. You'll be able to definitely obtain our Wifi hacker proper this moment at no cost and hook up with one of the networks detected by your COMPUTER cellular community greeting card. It's quite helpful out there for you particularly for individuals who have temporary web access. Cease risking your job!
These days, many Wireless networks are provided in every single place. However lots of them are secured by the password that is tough to get. The only strategy to get it is to compromise the Wi-fi network code. Indeed, our Wireless password hacker will help you to resolve your grievance with 100% safety. You'll be able to definitely obtain our Wifi hacker proper this moment at no cost and hook up with one of the networks detected by your COMPUTER cellular community greeting card. It's quite helpful out there for you particularly for individuals who have temporary web access. Cease risking your job! USB Loader GX Hack Who nonetheless uses game disks? The USB Loader GX mod generally is a disk emulating hack that permits gamers to load their favorite video games from a tough drive or SD card. The USB Loader GX hack permits avid gamers to load games at a quicker rate, choose from a library of games (with recreation Pirater mot de passe WIFI 2014 covers) and play completely different video games with out transferring away from their lazy bum and ejecting and inserting a brand new sport disk time and again. The USB Loader GX hack is probably the wifi cracker finest methods to “Pimp-out” (mod) your Nintendo Wii and can wow your friends.
USB Loader GX Hack Who nonetheless uses game disks? The USB Loader GX mod generally is a disk emulating hack that permits gamers to load their favorite video games from a tough drive or SD card. The USB Loader GX hack permits avid gamers to load games at a quicker rate, choose from a library of games (with recreation Pirater mot de passe WIFI 2014 covers) and play completely different video games with out transferring away from their lazy bum and ejecting and inserting a brand new sport disk time and again. The USB Loader GX hack is probably the wifi cracker finest methods to “Pimp-out” (mod) your Nintendo Wii and can wow your friends. If you want to improve the protection of your WIFI community you may view it as a transport layer solely, and encrypt and filter all the things going throughout that layer. This is overkill for the overwhelming majority of individuals, however a method you may do that would be to set the router to only enable entry to a given VPN server beneath your control, and require every client to authenticate across the WIFI connection throughout the VPN - thus even when the WIFI is compromised there are different harder layers to defeat. A subset of this behaviour is just not uncommon in massive company environments.
If you want to improve the protection of your WIFI community you may view it as a transport layer solely, and encrypt and filter all the things going throughout that layer. This is overkill for the overwhelming majority of individuals, however a method you may do that would be to set the router to only enable entry to a given VPN server beneath your control, and require every client to authenticate across the WIFI connection throughout the VPN - thus even when the WIFI is compromised there are different harder layers to defeat. A subset of this behaviour is just not uncommon in massive company environments. No doubt, this neighbor ought to have modified his password long ago, however there may be loads to admire about his security hygiene nonetheless. By resisting the temptation to use a human-readable phrase, he evaded a good quantity of reducing-edge sources dedicated to discovering his passcode. Because the code isn't likely to be included in any password cracking word lists, the only way mot de passe WIFI to crack it could be to attempt every eight-character combination of letters and numbers. Such brute-force attacks are possible, but in one of the best of worlds they require at the very least six days to exhaust all the probabilities when using Amazon's EC2 cloud computing service WPA's use of a highly iterated implementation of the PBKDF2 perform makes such cracks even tougher.
No doubt, this neighbor ought to have modified his password long ago, however there may be loads to admire about his security hygiene nonetheless. By resisting the temptation to use a human-readable phrase, he evaded a good quantity of reducing-edge sources dedicated to discovering his passcode. Because the code isn't likely to be included in any password cracking word lists, the only way mot de passe WIFI to crack it could be to attempt every eight-character combination of letters and numbers. Such brute-force attacks are possible, but in one of the best of worlds they require at the very least six days to exhaust all the probabilities when using Amazon's EC2 cloud computing service WPA's use of a highly iterated implementation of the PBKDF2 perform makes such cracks even tougher. One of the in style routers in use is the Cisco LinkSys. Out of the box, the default user name and password is 'admin' if you happen to don't change it out. When you don't change it out, you threat a hacker discovering your wireless sign, connecting to it, altering the password , and 'proudly owning' it. Plus after this you risk unauthorized utilizing both the computers attached to the router, and the hacker being able to 'use' your bandwidth to illegally obtain movies, music information and even send spam.
One of the in style routers in use is the Cisco LinkSys. Out of the box, the default user name and password is 'admin' if you happen to don't change it out. When you don't change it out, you threat a hacker discovering your wireless sign, connecting to it, altering the password , and 'proudly owning' it. Plus after this you risk unauthorized utilizing both the computers attached to the router, and the hacker being able to 'use' your bandwidth to illegally obtain movies, music information and even send spam.